Apr 8th 2025
Please be advised this transcript is AI-generated and may not be word for word. Time codes refer to the approximate times in the ad-supported version of the show
0:00:00 - Leo Laporte
It's time for security now. Steve Gibson is here. Lots to talk about including a 10.0 CVSS score for a problem in Apache Parquet. French school children are not gullible, it turns out. The French government tried to trick them and failed. And then we'll find out what multi-perspective issuance cooperation is and why you might need it. That and a whole lot more coming up next on Security Now Podcasts you love.
From people you trust. This is Twit. This is Security Now with Steve Gibson, episode 1020, recorded April 8th 2025. Multi-perspective issuance corroboration it's time for Security. Now the show. We talk about your safety, your privacy, your security and a bunch of other stuff that geeks are interested in. With this guy right here, I think you officially are the king of geeks, steve Gibson.
0:01:05 - Steve Gibson
I would wear that badge proudly, leo, wouldn't you? Yes, I would you have earned it over the years.
0:01:12 - Leo Laporte
Now 70 of them. Congratulations. That's amazing.
0:01:15 - Steve Gibson
We had a listener who had a t-shirt made and sent me a photo. Just say no to Port 80. I love it. From last week's podcast, which reminded me I had some made a while ago that just said Born to Code, because if I put on, I make a fresh cup of coffee. Put on some quiet music, sit down in front of my computer and have some problems to solve it is my happy place there's like there's like nothing like it.
0:01:51 - Leo Laporte
Yeah, that is just I get sad when I hear about vibe coding and ai replacing engineers, because I think it is independent of whether it's a useful economic exercise, a wonderful fun thing to do.
0:02:07 - Steve Gibson
A buddy of mine sent a link yesterday to a blog post. There's a guy named I think it's Ken Schiff, but that sounds like his last name, I've shortened it. Anyway, he's been. He like pops the lids on Intel chips, Intel processors, Wow. And then he takes photomicrographs of the chip and then reverse engineers the circuitry.
Wow about the times three multiplier hardware in the Pentium and that was like they had like a dedicated strip of silicon that was for multiplying by three. That's all it did. And then it was like, okay, why is there a hardware times three multiplier? And actually it's not difficult to multiply by three in binary right, because you just shift over by one and sum. But it turns out that they don't do binary multiplication, they do base eight multiplication in the hardware. It's like what, anyway? So this guy has just gone so into this and so I read the blog posting and I thought, you know this kind of thing.
The designers of that never were understood. They didn't get credit for it. I'm sure they were working within a small community of just incredible silicon design wizards and hopefully that was all they needed. But there's just there's like this incredible wizardry in stuff back then and it does feel like those days are leaving, sort of like turning coding over to AI. Those days are leaving, sort of like turning coding over to AI. Unfortunately, coding makes so much sense for AI because it is so rigorously logical and so complex and you should be able to say to an AI does this do what I want? And it would just say no, not even close.
0:04:21 - Leo Laporte
Well, you know, it's a computer talking to a computer. Of course it kind of makes sense that a computer would do that. Well, yeah, but at the same time it's like, you know, people in grade school, I know everybody said well, what am I learning? You know algebra, for I'm never going to use algebra. It's not about the algebra, it's about the pleasure of it and the kind of the formal reasoning which is a great thing to learn. I think coding should remain in the curriculum, even if it's not something you end up using.
0:04:52 - Steve Gibson
Well, and teaching math is much the same way. It's good for your brain to think in abstractions some of the time, which is why we have this podcast, leo, some of the time, which is why we have this podcast, leo. This is security now, episode 1020. Uh for patch tuesday. Uh, we actually have a picture that is apropos you. I think you're going to enjoy it when we get to it. Uh, today's title I wasn't sure it was going to fit. Uh, actually it. It strained the margins of the show.
0:05:24 - Leo Laporte
It's a little long and also a little obscure, I might add.
0:05:27 - Steve Gibson
It's very obscure. Yes, and it wasn't until my own description of the backstory behind this grew that I thought well, this is our topic for the week. Multi-perspective issuance corroboration, mpic Okay, the certificates, the issuance and the consumption for web browsers. Why they unanimously voted to require themselves to do this multi-perspective issuance corroboration. So this is a big change that just happened in the requirements for issuing web browser certificates, which we're going to get to after we look at Canon printer driver vulnerabilities enabling Windows kernel exploitation and the astonishing cybersecurity awareness which has been shown by a household appliance manufacturer.
A listener pointed me to this company. I think they're Australian or maybe they're, I don't remember where they are. Yeah, new Zealand, maybe. Anyway, unbelievable that they have a page because they're into connection and connected appliances. They understand what their obligation is if they're going to do it like none other. Also, france tried to hook two and a half million school children in a phishing test. We're going to look at the results of that. Wordpress, three years ago ago, added an abuse prone feature. Any guess what happened? And oracle is there something you would like to tell us that you have not so far?
0:07:38 - Leo Laporte
some problems over there. They're like what?
0:07:40 - Steve Gibson
no, nothing to see here, just we're. You know what's that big lump under the carpet? Don't worry about that. Utah's governor just signed the App Store Accountability Act into law. We've talked about the legislation passing through their lower bodies. It's now law in Utah. Now what? Also, it turns out that AI bots hungry for new data are inadvertently DDoSing FOSS projects. Yeah, this is a problem. Yeah, also, no Microsoft account. No, windows 11. A change been made to the dev channel coming soon, to your next Windows 11 installation Also. Gmail claims it now offers end-to-end encryption. Well, it kind of sort of does somewhat. It is the definition of a hack and we'll talk about it. Also, a dreaded CVSS 10.0 was discovered in something called Apache Parquet Not good, oh, sorry, sorry, but 10.0, 10.0, everybody, so that's as bad as it gets.
We got a bunch of listener feedback, believe it or not, had time for that too and then we're going to look at what is multi-perspective issuance, corroboration and why must all certificate authorities now do it, and, of course, we've got a great picture of the week, so I think maybe, leo, this podcast will finally be a good one.
0:09:18 - Leo Laporte
Finally after 1019 I think we got the hang of it now, there are people who's sunday.
you should stop by and say hello. Our 20th anniversary twit is this Sunday. After 20 years, Patrick Norton's going to come by, Samad Bulsamed will be on Alan Malventano and we're getting videos from all of our viewers. I've been asking everybody if you want to share your memory of the first time you saw a, your memory of the first time you saw Twitter, the first time you saw me and Steve, maybe back in the screensavers days, share a video with us. We've got a lot of them. It's going to be a lot of fun. That's on Sunday. Can you believe it? Long time we've been doing this.
0:09:58 - Steve Gibson
Steve Well, and I asked Benito. I said I thought that the number of Sunday's Twit was 1,027.
0:10:05 - Leo Laporte
It is, I think.
0:10:06 - Steve Gibson
And today is 1020 for us, so security now only started seven weeks later, right?
0:10:16 - Leo Laporte
Well, maybe because you never stop, you know, for the first 15 years you wouldn't even take the Christmas holiday off.
0:10:23 - Steve Gibson
So and maybe it was that tattoo that did it I thought I'm I'm quitting on christmas from now on there might be a few day, but, yeah, roughly seven weeks later was very quickly after it.
0:10:32 - Leo Laporte
Yes, yes, and you're coming up on your 20th right when, when is that going to be?
0:10:38 - Steve Gibson
do we know?
0:10:39 - Leo Laporte
august, I think yeah yeah 20 years. I don't feel that old, I really don't. It does you know? We started doing this in our late 40s.
0:10:51 - Steve Gibson
What's cool is that we have really been on the podcast through huge changes in the industry. Yeah, I mean, like you know, viruses moving from one person's thumb drive to the next, or computer to computer. I mean that was a thing, and you know.
0:11:11 - Leo Laporte
There's a great movie just came out called Black Bag. I don't want to spoil it. It's Michael Fassbender and Cate Blanchett and you should watch it. Have you seen it? No, but the only reason I mention this is there's a moment when they're talking about this exploit. That is a deadly exploit, and they said it's based on Stuxnet and we've designed it for air-gapped computers. And I was thinking, man, they must listen to security. Now, it was technically a really great moment in that movie. It's a fun spy movie. But you know what? That's one of the things I think maybe you could take a little bit of credit for. Hollywood is a little more savvy in the content, the computer content that you see on screen.
0:12:00 - Steve Gibson
I've been very impressed with what they're doing now I just think that it's percolated down into the culture.
0:12:07 - Leo Laporte
The people who are writing this now are part of the culture.
0:12:11 - Steve Gibson
Or they actually know we need to get a tech guy to help us with the script, and so there's some script. Apology. There was a series and I meant to mention it, except it wasn't that good, but it was about prime factorization.
0:12:28 - Leo Laporte
Yes, I was going to ask you. I haven't watched it, I was going to ask you about it.
0:12:32 - Steve Gibson
Yeah, it was known that our security infrastructure understood that it was possible to factor primes, so they didn't want it to be made public. So they were spying on all the top mathematicians who were working in the field that might stumble upon this. And so, anyway, it was. You know, I mean again, that's where I was thinking, wow, they got a lot of this right.
0:13:15 - Leo Laporte
I was ready to lambaste them. I thought this is going to be terrible.
0:13:19 - Steve Gibson
Well, there were some things that were not correct. They didn't actually say it wasn't factorization, but it was primes. They understood that primes.
0:13:26 - Leo Laporte
Something about primes something about primes.
0:13:28 - Steve Gibson
oh, it was patterns in primes. It was some guy was like, oh, he's like figured out that like a pattern in primes, but it turns out that this, so this was a conspiracy to keep this from being discovered. Keep it quiet, to keep it quiet. That went back decades, and so, anyway, I would say it was fun.
0:13:49 - Leo Laporte
And you and I both watched Robert De Niro's Zero Day, which also had some technical accuracy in it, so you know they're getting better. Anyway, time to take a break. Nothing but technical accuracy just around the corner and our picture of the week with first, also technically accurate. Yes, is it? Oh good, I haven't looked yet. All right, I like to save it for the show, our show today, brought to you by a brand new sponsor, material.
This is something everybody needs. Gosh knows we need it. It's the multi-layered detection and response toolkit for email. I think we all know email is one of the primary vectors these days for malware. So phishing spear, phishing attacks and so forth.
Your cloud office isn't really another app. It's the heart of your business. It is for us, right? Uh, we, we use Google Cloud. Maybe you use Microsoft 365. But traditional security tools aren't really designed for that kind of cloud architecture. They treat email documents as afterthoughts. Meanwhile, your most critical assets are remaining exposed. So that's where Material comes in.
Material transforms cloud workspace protection with a. I think I talked to them the other day. I was blown away. A revolutionary approach. It goes beyond the kind of traditional security paradigms. Let me. Let me kind of explain this as I best I can. You get dedicated security for modern workspaces google workspace, microsoft 365. Purpose-built protection is designed specifically for those platforms and it's across the entire security lifecycle, so it defends your organization before, during and after potential incidents. It doesn't just block them, it's there for you no matter what happens. Material allows you to scale security without scaling your team, using intelligent automation to multiply your security team's impact. Material provides security that respects how people work. That's really important, right? Because if security is hard to use or gets in people's way, they'll go around it. It eliminates that impossible choice we're all familiar with between robust protection and productivity. They've really managed to make it work.
Material delivers comprehensive threat defenses through four critical capabilities. Of course, there's phishing protection that's job one. Ai power detection that identifies sophisticated attacks. And what I like about Material it doesn't delete the email, it doesn't take it off the server, it just protects you from it and identifies, identifies it so you can look at it and say, yeah, that's a phishing attack, I'm glad we dodged it, or no, that wasn't a phishing attack, and you can recover the email. So they've done this very nicely. They also help you with data loss prevention, intelligent content protection and sensitive data management. Posture management. They identify misconfigurations and risky user behaviors that's fantastic. And identity protection. They have comprehensive control over access and verification. And, what I love about this, you don't have to filter your email through their servers. They use built-in APIs of both Google Workspace and Microsoft 365 to do all of this, so it's really an easy thing for you to implement, set up and you don't give over control of what your email system is doing.
Right, the head of security at Figma. They love it. At Figma, by the way, they said this about Material Quote it's rare to find modern security tools with a pleasant, usable UI being at Figma, obviously. Obviously, we're attracted to well designed interfaces. Materials interface was just so smooth and slick. From automatic threat investigation to custom detection workflows.
Material converts manual security tasks into streamlined, intelligent processes. By the way, you need it that way because you need to be able to respond over and over again instantly, right? Humans just can't do it. You got to have assistance, you got to have automation. They also provide visibility across your entire digital workspace so your security team can focus on strategic initiatives instead of endless alert triage. And if you're on a security team, I think you know what I'm talking about protect your digital workspace, empower your team, secure your future with material. It's really cool.
You can actually go to materialsecurity. That's their website, materialsecurity. You can learn more there. You can book a demo. They have a self-running demo you can take a look at. You can actually see what it looks like when you get a phishing email and the process and so forth, and I love it that it's API-based. They don't mention it in the copy here, but I was really blown away. Both Google Workspace and Microsoft 365 have very capable APIs that let this third party really do all the security you need without redirecting your email. It's materialsecurity. Check it out. It's really important if you're using, as we do, google Workspace or Microsoft 365. All right, let us go back to the show and Steve Gibson's picture.
0:18:55 - Steve Gibson
Those security domains cost $2,500 a year. Oh, you looked at it, I bet, and I don't think that's in keeping with the founder's intent for the way the internet would work.
0:19:07 - Leo Laporte
That's expensive. Yeah, these custom emails really, you know, but on the other hand they're nice, like I have leopizza and I think, if you wanted to, well, all right, let's look at the. Let's look at the picture of the week.
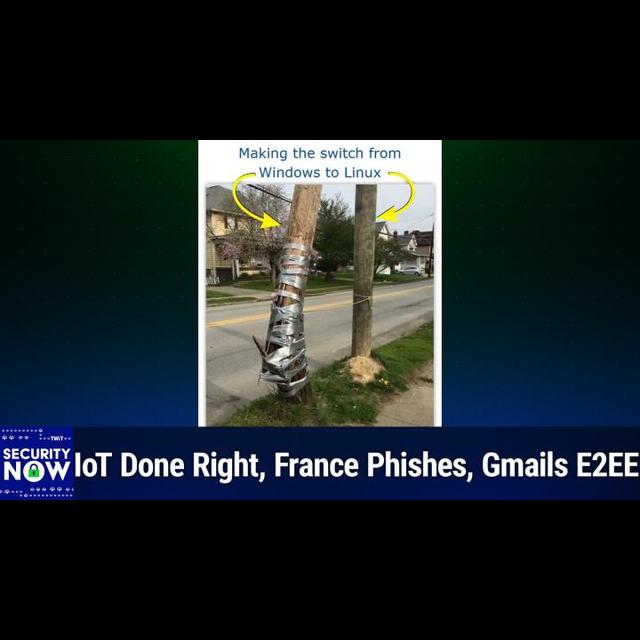
0:19:24 - Steve Gibson
Mr Gibson, I'll scroll up here I gave the caption making the switch from windows to linux I'm trying to understand a poll of last week's podcast about the eu os.
0:19:37 - Leo Laporte
If you scroll all the way up, you get it a little bit better. Okay, okay, broken telephone pole.
0:19:43 - Steve Gibson
Ah, yes, and again, these pictures beg so many questions. So for those who can't see, we've got a buckling, broken telephone pole that some hapless lineman has tried to keep erect with duct tape. Oh my God, duct tapes keeping the world together. It looks like maybe there's some sticks on the outer side that were used Like splints Some splints, exactly so it was like splinted and then duct tape.
The splints were duct taped to the pole, just trying to keep it up. But then over to the right, we see the one that I've labeled Lennox, which has like a new pile of dirt at its foot.
0:20:33 - Leo Laporte
It's the replacement pole, clearly.
0:20:35 - Steve Gibson
Exactly it must be, and then I don't know why there's a little rope strung between.
0:20:39 - Leo Laporte
That's the funniest thing. I don't understand that either. It's like a leash. It's like don't go away, boy. I don't understand that either. It's like a leash. It's like don't go away, boy, stick close. That is the funniest thing ever, duct tape man. It holds the world together. It is yes, exactly, and Windows is the duct tape solution. And, of course, the brand new perfectly formed pole is Linux. I like that, steve.
0:21:02 - Steve Gibson
Thank you, that's right. It's one of the expressions we have around the house. When one of us wakes up and something is stiff, we say, oh, get the duct tape.
0:21:11 - Leo Laporte
Really okay, I'm not sure that was maybe a little too much information oh, like a stiff muscle, is what?
0:21:17 - Steve Gibson
oh, like a shoulder. Yes, indeed shoulder, sorry shoulder, of course. Get the duct tape, you never that's right.
0:21:25 - Leo Laporte
I have a vision of you duct taped to the bed.
0:21:28 - Steve Gibson
Okay, so maybe that's not uh, okay, so uh, the microsoft offensive research and security engineering. This is one of those reverse engineered acronyms, the the abbreviation is MORSE M-O-R-S-E Microsoft Defensive Research and Security Engineering. They've identified a crucial security vulnerability within a range of Canon printer drivers Canon, you know, being a leading, very popular printer which threatens users across well, anybody who's using that printer who would be a target. The vulnerability could reportedly allow malicious actors to compromise printing operations and, in severe cases, execute arbitrary code on affected systems. We did a podcast years ago that I thought was one of our better ones, where we looked at the threat that something as innocuous-seeming as a network printer in an enterprise could pose, because it was discovered that advanced, persistent threat actors were actually setting up shop in enterprises' printers which were not being scanned. You know they didn't have Windows Defender running on them, it was just a printer, but turns out, you know, it's a computer, probably running Linux of some flavor, and they were able to just stay ensconced inside this printer for quite some time. Anyway, this has a CVSS.
The concept of a printer driver in this case not the printer itself, but the printer driver in a Windows system has a CVSS score of 9.4. As we know, that's a high severity risk. It's up at the high end of the scale and it has a 9.4 due to its lack of complexity, very easy to leverage the bugs in these Canon printer drivers. You do not need any elevated privileges to use it, nor any user interaction. The potential for high impact compromise of confidentiality is there, so 9.4. It provides a path to deliberate memory corruption during the EMF recode processing, which is something that the printer driver does Probably. Emf is enhanced metafile, I'm pretty sure, and unfortunately this opens systems that do not use Canon printers to the infamous BYOVD attacks. Where BYOVD is short for bring your own vulnerable driver.
The problem is these vulnerable Canon printer drivers were originally signed by Microsoft. You know Microsoft blessed them, allowing them then to be loaded without a second thought into Windows. So they can't be altered at all, or that would break the signature and then Windows would refuse to load the driver into the kernel. No need to alter the driver because it's buggy. And now the bugs have been found. So malware can bring along one of these flawed Canon printer drivers, drop it onto the system, get it loaded into the kernel and then leverage the flaw in order to take over the system. They are when an entity has Canon printers, they're there by default across a variety of printers, including their production models, home and office automation, multifunction printers and laser printers. So all that a malicious application needs to do is cause a print job to be processed through the vulnerable driver that allows the attacker to gain control and have kernel-level access, which is to say root on the system. Canon has acknowledged the issue and has promised to be releasing updated drivers as soon as they can. So if you are a Canon user, that means your system already has these vulnerable drivers in it and the malware doesn't need to bring its own along. So keep an eye out for any updates that the Canon offers. You'll certainly want to make sure that you are receiving Canon's notifications of updates, and I imagine that what will happen as soon as the new drivers are present and given some opportunity for them to filter out into the ecosystem is that before long, windows Defender and the other endpoint management you know third-party software will start explicitly looking for these known vulnerable drivers and say you really don't want to be loading this, and that's the way the bring your own vulnerable driver problem will get resolved. Is that, as soon as replacements are available so that functionality isn't killed when the vulnerable driver is removed, then those drivers will just be blacklisted and you won't be able to load them into Windows anymore. So all this takes time and, as we know, everything now is an arms race to see how much infiltration and how much damage can be done before the problem is resolved.
Okay, I talked about an astonishing home appliance company. This was thanks to a piece of feedback that we received from a listener, dave Morel. David wrote every home IoT device maker should follow the lead of this home appliance maker. About the only thing. And Leo, I have to say, when I was looking at this site, I thought oh, these look like appliances Leo would want. I mean, they are really beautiful. Don't tempt me, steve. The company is Fisher Paykel. Yep, you got it up on the site.
Now, he said about the only thing they could have added is advice to use a YubiKey or similar, meaning they really get it. And he said they really get it. He said and it even looks like you can buy these. Oh, they're New Zealand. You can buy these. New Zealand made home appliances in the US. Personally, home appliances in the US. Personally, I'm quite happy not having IoT in my home appliances. Okay, so David's note made me curious. I went over to the Fisher Paykel website it's F-I-S-H-E-R-P-A-Y-K-E-Lcom and I discovered that they have an entire page devoted to the cybersecurity of their well-connected appliances. So to give everyone a sense for what's there on this home appliance makers site, they wrote we're vigilant about securing your connected appliance. We understand that the security of our products is of the utmost importance to our customers. We build appliances around these core security values. The fact that they even know the term core security values.
0:28:58 - Leo Laporte
They use WPA3. That's all I needed to see. It's like wow, wow, must be a geek in there somewhere.
0:29:06 - Steve Gibson
I have to say, leo, I wonder if someone's going to be smiling when he hears me reading this because he's a Security Now podcast listener. I mean because, like I mean some guy at Fisher Paykel because it feels like it, doesn't it?
0:29:20 - Leo Laporte
It sounds like it's everything you would say the guy's been listening to us.
0:29:24 - Steve Gibson
It sounds like the guy's been listening to us. The page says security is ingrained in our business culture and in the way we developed your connected appliance. It's a business policy that security is built in to every aspect of our process. It's built in during all phases of development, manufacturing and maintenance. Your appliance is secure without user configuration or specific router settings. He said security by design. Security controls to protect appliance data, user authentication and authorization and how the system will be securely maintained are integrated into the functional features of the appliance. The software meets industry best practice coding standards who talks about the coding of their dishwasher? And is developed by the test-driven development software method.
0:30:29 - Leo Laporte
Yeah right on.
0:30:31 - Steve Gibson
The guys must have like some nephew who's into serious security or something. This is just amazing, they said. Any third-party and open-source software is analyzed for security and the safety of your appliance and data Prior to deployment. The appliance undergoes extensive software security and performance testing. Security penetration testing on the connected system and its components the appliance, mobile app and cloud is done regularly. Post-development, post-deployment, software updates are released to ensure the appliance has the latest security code to protect your appliance and data. I mean I almost want to buy this stuff just to support these people. It's amazing, they said.
Under security by default, every connected appliance has all security features enabled when the appliance is first connected. No special configurations or specific router settings are needed to your Wi-Fi router. Using the WPA3 network security protocol as standard, with WPA2 for backwards compatibility, the appliance does this even if your router is not set to this configuration. That's just one example so awesome Of how security by default is engineered into your appliance. And then defense in depth Every component of our connected appliance ecosystem has security controls that provide independent redundancy to protect against malicious attacks. We ensure security controls are implemented in layers for data protection at rest and in transit.
0:32:29 - Leo Laporte
I wish these guys made like some social networking software because we could give it to our government and it would be way more secure than what they're using.
0:32:39 - Steve Gibson
They said this layered approach strengthens the security of our entire ecosystem. We're continuously testing and reviewing the security systems. If needed, these layers can be updated and improved by software updates and for transparency, our security controls and methodologies are industry standard. Our goal is to communicate our additions with openness and accountability. We're industry leaders in IoT security and promote transparency to help educate our customers. Reach out to us if you have any questions or concerns. Please see below under our ratings section for current evaluations of our appliance products they look pretty darn good.
0:33:27 - Leo Laporte
You're right, steve, and you can buy them in the us. They're gorgeous. I mean, the equipment is beautiful leo.
0:33:33 - Steve Gibson
Yeah, I mean, it's who the? The people who did the industrial design are friends with the people who did the security design. I mean it is top notch look at that.
0:33:44 - Leo Laporte
Yeah, we're in. Also top prices fifteen thousand dollars for an oven oh, but honey, it'll sing you to sleep I have uh internet connectivity on my uh, on my oven, of course you do. The only value at all is it will um, it will tell you when the oven's preheated. On your phone said Say hey, your oven's ready, go put your roast in. Go put your roast in, it's ready.
0:34:09 - Steve Gibson
That's it, door's open Industry leaders in IoT security. Actually, we could use that for our refrigerator.
0:34:17 - Leo Laporte
Luckily, our refrigerator sounds an alarm Beeps at you.
0:34:19 - Steve Gibson
Yeah, Lori just walks away. I don't know what is going on, but it's like honey, you know, not only are the lights on, but the refrigerator is open.
0:34:27 - Leo Laporte
So yeah, I've done that, anyway, reach out to us.
0:34:30 - Steve Gibson
They said if you have any questions or concerns, please see below under our rating section for current evaluations of our appliance products. We ensure these best practices are applied to your appliance and its IoT ecosystem through regular penetration testing. We work with ethical hackers and security researchers to evaluate the security of your smart appliance and system through third-party evaluations. It's just astonishing. And then they said under our ratings, we are proud to have achieved the gold verification level for UL's. You know Underwriter Laboratories IoT security rating? I didn't know. Underwriter Laboratories did IoT security rating. With thorough evaluations conducted every year since we first achieved this rating, we continually demonstrate gold-level security capabilities that align with industry best practices. This is an oven, folks. This is not like a server or a router or an endpoint security device. This is somebody's microwave.
Unbelievable, astonishing so anyway, props and a salute to FisherPayCalcom and if anyone from there is listening to this podcast, congratulations. Oh and Leo, if you suspect that your appliance has been compromised or you have identified a security vulnerability in one of our connected appliances, we urge you to contact our appliances security incident response team. Holy cow, wow At is at fisherpaykelcom, and here it comes. Note we support PGP encryption using the Fisher and paykel appliances.
0:36:26 - Leo Laporte
Information security, pgp key all, right now I'm going to give you the bad news. Oh, it's a subsidiary of hire, which is a giant chinese multinational. So, um, I mean, you know, maybe they could, maybe they could spread the word throughout the entire hire ecosystem.
0:36:49 - Steve Gibson
I wonder if they probably use open source but don't publish their firm?
0:36:52 - Leo Laporte
Yeah, I mean, I think nowadays every this company was acquired, obviously yeah, it hires a giant monster conglomerate.
0:37:06 - Steve Gibson
Right. So they just sucked him up because they said, these guys are doing it right, we want their-.
0:37:10 - Leo Laporte
They have to have a high-end brand, right. We want a piece of their action, Just as they have low-end brands. Yeah.
0:37:16 - Steve Gibson
Oh, and get this, Leo. I couldn't imagine, After all, that they then have a sort of an FAQ Q&A thing where they talk about to their customers how to enhance their security and they finish with separate networks and secure networks dedicated for your IoT devices which makes me think, are they listening to this podcast? That separate from your network used for banking or e-commerce activities, or that which handles your most private and sensitive data? You can further segregate your networks based on the IoT device itself. There are two methods for this when using one internet connection, using one router and setting up a guest access or a guest network within the router settings, or use separate routers paired with your internet connection.
0:38:17 - Leo Laporte
Oh, they definitely listen to this show.
0:38:23 - Steve Gibson
Incredible. If you choose to set up a guest network, ensure the password for the guest network is strong and, if available, ensure that access to local network resources is turned off. This may also be called isolate, and it's a good thing. This is April 8th and not last week's April 1st podcast, because this would have made the best imaginable April Fool's spoof, since no one would ever believe that I hadn't made this entire thing up from scratch. You know, and Leo, if the rest of the world designed and built their equipment like these guys, it feels as though our job here would be done.
0:39:08 - Leo Laporte
That's impressive. I wish all IoT stuff was like this. That's incredible, yeah.
0:39:15 - Steve Gibson
Well, we're going to talk about France's phishing test after you tell our listeners how it is that we're still here.
0:39:22 - Leo Laporte
Ah, that's a very good question after uh almost 20 years. Well, I think we could safely say it has a little bit to do with our fine sponsors, steve. Oops, that is not what I want to show you. What is that? We go uh, our uh show today, brought to you by and I think you know this company, we've mentioned it before threat locker. Really cool company. Um, I think if you listen to the show it's pretty clear ransomware is just devastating uh companies.
0:40:01 - Steve Gibson
Remember that site are the ransomware listing site.
0:40:05 - Leo Laporte
Every day another dozen.
0:40:07 - Steve Gibson
I looked again. It was astonishing.
0:40:10 - Leo Laporte
It's mind-boggling. They're doing it with phishing emails. They're doing it with infected downloads, malicious websites, rdp exploits. I'm going to make a t-shirt that says close port 135. Don't be the next victim.
Threat Locker's zero trust platform. This is really. This is the gold standard in security. Zero trust takes a proactive, deny by default approach. It blocks that's the key, by the way. Deny by default. It blocks every unauthorized action, protecting you from both known and completely unknown zero-day never heard of it before custom-coded just-for-you threats. It's trusted by big companies and small global enterprises like JetBlue, infrastructure companies like the Port of Vancouver. You know, if you're a seaport and you've got container ships coming in and an entire region and, in case of the Port of Vancouver, probably entire country relying on your being reliable and up, you need to protect yourself. They use ThreatLocker to shield themselves from zero-day exploits and supply chain attacks, and this is great provide complete audit trails for compliance.
Threatlock lockers innovative ring fencing technology isolates those critical applications from weaponization. It stops ransomware. It limits lateral movement within your network. It really works, and in all industries. In fact, it even supports mac environments. So no matter, even if you have a heterogeneous network, this is a great solution, very affordable. By the way go. Look at the pricing. I was stunned. Any company should do this. It's totally affordable. They provide 24 seven us-based support. You get comprehensive visibility and control.
Here's from another governmental organization that cannot afford to be ransomware Mark Tolson. He's the IT director for the city of Champaign, illinois. You know this is a perfect example, because they are a mission critical operation, but they don't have an infinite budget, right? Threat Locker is a great solution. Here's what Mark says. He says, quote Threat Locker provides that extra key to block anomalies that nothing else can do. If bad actors got in and tried to execute something, I take comfort in knowing threat locker will stop that. That's the beauty of threat locker zero trust. Stop worrying about cyber threats. Get unprecedented protection quickly, easily and cost effectively with threat locker. All you have to do to find out more and get a free 30-day trial is go to ThreatLockercom slash twit. Learn more about how ThreatLocker can help mitigate unknown threats and ensure compliance at the same time. Threatlockercom slash twit. We thank them so much for supporting the show and please use that address so they know you saw it here ThreatLockercom slash twit. Oh, I'm on the wrong side.
0:43:12 - Steve Gibson
Switching around.
All right, Steve, Okay so the French government recently conducted a large-scale phishing test targeting more than 2 a half million middle and high school students. The bait was a link that advertised cheats and cracked games, which instead redirected any students who were foolish enough to click on it to a fishing awareness video. Now, what was interesting was, according to France's Privacy Watchdog, over 210,000 students did click the link, but that's only one in 12 students out of a population of two and a half million. Impressive, yes, eight percent out of a population of two and a half million. Yes, 8%. And you know, while, yes, 210,000 is a lot of individual students, they fared way better than the one-third click rate which is typically seen in corporate environments. So the old folks in the corporations, it's like oh, oh, I can get free socks for life, great. But you know, these kids are like I don't think so. This looks like junk. So congratulations. Um, as we've observed before, with 521 million websites built on WordPress 521 million, that's mind-boggling it is.
It's like 43.5% of all websites in the world are WordPress, so it's security WordPress's security is always a top concern, so much of the internet depends upon it. So when three years ago, in 2022, wordpress added a feature attackers could only dream of having, it's hardly surprising that it didn't take long for it to be abused. Wordpress's site describes this nifty new feature known as must-use plugins. It's like what could possibly go wrong? Which is, you know, our rhetorical question? They said this is how they described this feature.
Must use plugins, aka MU-plugins, are plugins installed in a special directory inside the content folder and which are automatically enabled on all sites. In the installation, must use plugins do not show in the default list of plugins on the plugins page of WP-admin, although they do appear in a special must use section, and they cannot be disabled except by removing the plugin file from the must use directory which is found in WP-content slash mu-plugins. By default For web hosts, mu plugins are commonly used to add support for host-specific features, especially those where their absence would break the site. Must use plugins are always on with with no need to enable via admin, and users cannot disable them by accident. They're enabled simply by uploading a file to the MU plugins directly without having to log in.
Even this, of course, as I said, is where we cue one of our favorite rhetorical questions what could possibly go wrong? Yes, you just have the file there and WordPress won't show it to. The admin, won't require you to be logged in to enable it. In fact, you can't enable it. It's always enabled and you can't disable it because they said, well, it would break the site if this plugin wasn't there. So we're just going to if it's present in this directory run it.
Godaddy's security team provides the answer to the question about what could possibly go wrong, and unfortunately that's not rhetorical To no one's surprise except, I suppose, the creators of this very abuse-prone feature. I mean, they must be surprised, but, like duh, hackers are now abusing this little-known WordPress feature to install and hide their malware from site admins. According to GoDaddy's team, threat actors have been found to be abusing, to no one's surprise, must use plugins since at least February of this year, and that abuse has recently grown worse. It's like hey, this works, let's use it everywhere. Hackers are breaking into WordPress sites and dropping malware in the MU plugins folder, knowing it will get automatically executed and won't show up in the site backend management as an added benefit. Because it's a relatively unknown and under the radar feature, many WordPress security tools don't even scan the MU Plugins folder for threats. They're not even looking. Securi has seen attackers use MU Plugins folder to deploy backdoors and web shells, host SEO spam on hacked sites, as well as hijack and redirect traffic to malicious sites. The wide and widening spectrum of abuse suggests this feature is gaining popularity and traction among underground groups. A security analyst said quote many infections inside the MU plugins directory suggests that attackers are actively targeting this directory as a persistent foothold.
Wordpress site owners and admins are advised to keep a watch on the content of that folder If it's currently empty, unused and unneeded, unused and unneeded, deleted entirely and make sure it stays deleted. So, stepping back from all this, it appears that the design of this makes it far too easy to both use and abuse. With a design like this, it's not possible to have ease of use without also inviting ease of abuse. So again to our listeners. Given that more than 500 million sites, or more than 43% of the Internet, is WordPress, it must be that a big chunk of our listeners are affiliated one way or the other with sites that are being run by WordPress. So take a check. It's under the WP-content directory, the default content directory, mu-plugins. It's probably empty. Plugins it's probably empty. You know WordPress brought it along for the last three years, since 2022. It's more than likely.
Whatever your host is, it doesn't need it, but it's there waiting to be abused. First of all, make sure that, if there's anything in there that you know what it is and why it's there, get rid of it and get rid of its directory if you don't know that you know what it is and why it's there, get rid of it and get rid of its directory. If you don't know that you need it because this is under active exploitation, they do have to break in somehow first, but achieving persistence or planting malware somewhere where it won't be found and quickly discovered is the second part of the challenge, and quickly discovered is the second part of the challenge. And if it's a WordPress-based site and the MU plugins directory is there just waiting to run something that you drop in, that's what the bad guys are going to do Meanwhile, meanwhile, meanwhile.
Oracle, the massive organization with designs on running TikTok although I thought that was interesting, leo. By the way, we should mention that on Sunday's Twitch show, you had Jason Calacanis, who he's a great guest. You've had him through the years. Yeah, he's an old friend, he's an old friend?
yeah, he's an old friend, super smart guy, um, and he he happened to mention. The thing that made me think of it is he was thinking that amazon right is. Wasn't that what jason thought?
0:52:16 - Leo Laporte
he said amazon's going to be, uh, the tiktok, uh, yeah, we'll see, manager, we'll, we'll see what?
0:52:23 - Steve Gibson
what we'd heard was that it was going to be oracle, that that down in texas you know, down in Texas, the big database company and they were going to be managing TikTok and retaining TikTok's US domestic data. Anyway, whether or not that happens, whether it's Oracle or Amazon, and TikTok just got another 75-day extension right Because the boom was about to be lowered on it again.
0:52:48 - Leo Laporte
Yeah, Saturday was the deadline.
0:52:50 - Steve Gibson
Yeah, okay, so Oracle appears to be having a problem with confession. According to Bloomberg sources, hackers breached Oracle Health and stole medical data from the company's servers. The hack took place well back at the end of January and the hackers are using the stolen data to extort US medical providers. So this is not apocryphal. This actually happened. Yet Oracle has said nothing. They've made no report of any breach, as is required by law, to the? U, the company's cloud service. In early March, lawrence Abrams wrote about this for his bleeping computer site under the headline Oracle customers confirm data stolen in alleged cloud breach is valid, lawrence wrote. Breach is valid, lawrence wrote.
Despite Oracle denying a breach of its Oracle Cloud federated single sign-on login servers and the theft of account data for 6 million people, bleeping Computer has confirmed with multiple companies that associated data samples shared by the threat actor are valid. Last week, a person named Rose87168 claimed to have breached Oracle cloud servers and began selling the alleged authentication data and encrypted passwords of 6 million users. The threat actor also said that stolen single sign-on and LDAP passwords could be decrypted using the info in for companies and government agencies that were allegedly impacted by the breach. It should be noted, wrote Lawrence, that some of the company domains look like tests and there are multiple domains per company. In addition to the data, rose 87168 shared an archiveorg URL with Bleeping Computer for a text file hosted on the loginus2.oraclecloudcom server that contained their email address. This file indicates that the threat actor could create files on Oracle's server indicating an actual breach. However, oracle has denied that it suffered a breach of Oracle Cloud and has refused to respond to any further questions about the incident. The company told Bleeping Computer about the incident. The company told Bleeping Computer, meaning Oracle told Bleeping Computer, quote there has been no breach of Oracle Cloud. The published credentials are not for the Oracle Cloud. No Oracle Cloud customers experienced a breach or lost any data. Unquote, he said. This denial, however, contradicts findings from Bleeping Computer, which received additional samples of the leaked data from the threat actor and contacted the associated companies. Bleeping Computer reached out to the affected companies. Representatives from these companies, all who agreed to confirm the data under promise of anonymity, confirmed the authenticity of the information. The company stated that the associated LDAP display names, email addresses given names and other identifying information were all correct and belonged to them, were all correct and belonged to them.
The threat actor also shared emails with Bleeping Computer, claiming that it was part of an exchange between them and Oracle. One email shows a threat actor contacting Oracle's security email secalert underscore us at oraclecom to report that they had hacked Oracle's servers. To report that they had hacked Oracle's servers. Quote I've dug into your cloud dashboard infrastructure and found a massive vulnerability that has handed me full access to info on 6 million users. Unquote reads the email seen by Bleeping Computer. Another email thread shared with Bleeping Computer shows an exchange between the threat actor and someone using a Proton email address who claims to be from Oracle. Bleeping Computer has redacted the email address of this other person as we could not verify their identity or the veracity of the email thread. In this email exchange, the thread actor says someone from Oracle using an at protonme email address told them that. Quote we received your emails. Let's use this email for all communications from now on. Let me know when you get this. Unquote.
Cybersecurity firm CloudSec S-E-K has also found an archiveorg URL showing that the loginus2.oraclecloudcom server was running Oracle Fusion Middleware 11G as of February 17th of this year, 2025. Oracle has since taken this server offline after news of the alleged breach was reported. This version of oracle software was impacted impacted by a vulnerability tracked as CVE-2021-35587 that allowed unauthenticated attackers to compromise Oracle Access Manager. The threat actor claimed that this vulnerability was used in the alleged breach of Oracle's servers. Bleeping Computer has emailed Oracle numerous times about this information, but has not received any response. So, in the face of this overwhelming evidence, which arguably borders on proof, oracle has deliberately chosen to remain entirely silent, even though doing so is a clear breach of reporting law.
The US Securities and Exchange Commission mandates that publicly traded companies adhere to specific reporting requirements following a material cybersecurity incident, such as a database breach affecting US citizens. These requirements, which have been effective since December of 2023, are designed to ensure timely and transparent disclosure of significant cybersecurity events. Specifically, within four business days after discovering that a cybersecurity incident is material, publicly traded companies are required to file a Form 8K disclosure under Item 1.05. That disclosure must include the nature, scope and timing of the incident. The nature, scope and timing of the incident, the material impact or reasonably likely material impact on the company's financial condition and results of operations, and determination of materiality. Companies are required to assess the materiality of an incident without unreasonable delay upon discovery. Oracle knows this. Reasonable delay upon discovery Oracle knows this.
Yet nothing about either of these clearly material major breaches has been publicly disclosed and I would argue I mean you know Lawrence did a beautiful job of you know, really pursuing these facts and essentially demonstrating proof of a material breach and the fact that they had a server running known buggy and patched four years ago authentication front end and the attacker said that's the bug they used to get in. And now that server is gone, I mean it's seems like an open and shut case and Oracle is really misbehaving badly. So, for what it's worth, unfortunately, you know, their, their lack of responsibility taking is exposing the authentication credentials for 6 million people who trust them. So it's not like this is nothing. This is not good. And those 6 million authentication credentials are now for sale on the dark web and apparently there's a means of decrypting them using information that the attacker also has. So you know this is not just, you know, oracle choosing not to say anything because they don't want to affect their, their stock valuation, it's also materially hurting their customers. I mean this is, you know, a class action lawsuit against them pending. It's hard to see how it wouldn't be. Not that you or I are in favor of that, but they need to take responsibility.
Meanwhile, I wanted to note that nearly two weeks ago, as we mentioned two weeks ago, that Utah law we talked about, which had passed through their legislature, was now signed into law by Utah's Governor Spencer Cox, formerly known as the App Store Accountability Act or SB 142. The new law mostly takes effect a little over one year from now. So, as always when some new law goes into effect, that is going to require a significant change in behavior. Then a period of time, a grace period, that's the word I was looking for a grace period is part of the law to allow people to get themselves ready. That occurs on May 6th of 2026, given that the law stays in effect until that time, it's on May 6th 2026, a little over a year from now, that the law's core requirements, including age verification and parental consent mandates, will take effect. So that'll give you know, the app stores, developers, regulators time to prepare for coming into compliance with these new regulations and, of course, it will give other states time to decide if they want to follow suit.
As we discussed, this will require Apple and Google's mobile app stores to verify user ages and require parental permission for those under 18 to use certain apps. The law is the first of its kind in the US and represents a significant shift in how user ages are verified online. The law states that it's the responsibility of mobile app stores to verify ages, which shifts the onus to Apple and Google, as those who run the stores, and away from the individual apps like Instagram, snapchat and X to do the age checks. This does beg the question, though what about apps that are already downloaded and installed from app stores? When May 8th rolls around next year, are those grandfathered in because they're already there and they're allowed to stay without verification, or will they need to then be re-verified? Don't know.
Regardless of the passage of this App Store Accountability Act, it's expected to trigger something. South Carolina and California have both been rattling their sabers, saying that they're looking into doing this. One of the bill's sponsoring senators said that the new law is designed to protect children who may not understand apps terms of services and therefore are unable to agree to them meaningfully. Meaningfully, todd Wheeler said. Quote for the past decade or longer, instagram has rated itself as friendly for 12-year-olds. He says it's not.
So the Utah law is expected to face legal challenges and fights over its validity, but, as we know, my own take on that, on this whole thing, is that, yes, in cyberspace, something needs to be done. If, if we're going to decide that that children's age matters, then responsibility needs to be taken somehow that the most recent begrudging proposals that have been made by Apple and Google make the most sense. App Store apps need to carry API-readable age-appropriate indicators, and the devices being used by minors may need to obtain parental permission before inappropriate applications can be downloaded and or used on age-restricted devices, and that solves the problem. The apps don't obtain any information about the ages of their users and the devices are responsible for getting permission if they've been configured to require it. So you know, apple and Google have both articulated that solution, and I imagine that we're going to see that happen.
And that'll be good and not a huge loss of privacy. This was an interesting piece. I guess you saw that, leo. It turns out that AI bots are inadvertently DDoSing FOSS you know, free and open source software repositories in their endless quest for more publicly available content.
1:07:59 - Leo Laporte
Yeah, wikipedia has been complaining about this. It's a real problem for them.
1:08:03 - Steve Gibson
Yeah, oh, Wikipedia has. Yeah, think about it, God. I guess that makes sense, right.
1:08:07 - Leo Laporte
Yeah, Wikipedia is a great resource and they want to be a public.
1:08:12 - Steve Gibson
I mean they want to not restrict themselves to you know in any way, they want to be a public resource. Wow. So Ars Technica did a great job of reporting on this worrisome trend that's been developing and worsening through the year. They said software developer Zayaso reached a breaking point earlier this year when aggressive AI crawler traffic from Amazon overwhelmed their Git repository service repeatedly causing instability and downtime. Despite configuring standard defensive measures, adjusting robotstxt, blocking known crawler user agents and filtering suspicious traffic, I also found that AI crawlers continued evading all attempts to stop them, spoofing their user agent strings and cycling through residential IP addresses, using them as proxies. So you know, actively working to avoid being blocked.
Desperate for a solution, I also eventually resorted to moving their server behind a VPN and creating Anubis, a custom-built proof-of-work challenge system that forces web browsers to solve computational puzzles before accessing the site.
Basically, proof of work in the browser. Again, solve computational puzzles, so spend time per access, per query, to validate themselves. We've probably run across this on Cloudflare. Sometimes you'll come to a Cloudflare page where it'll just sort of hold you for a while while something appears to be going on, and that is typically a proof of work requiring some script in your browser to do some heavy lifting which no high rate bot is able to afford, because every single time the bot tries to access it is hit with this, this barrier to entry, essentially so ours wrote that that I also had wrote in a blog post titled a desperate, quiet cry for help. He said it's futile to block AI crawler bots because they lie, change their user agent, use residential IP addresses as proxies and more. I don't want to have to close off my GitT server to the public, but I will if I have to. Ioso's story highlights they wrote a broader crisis rapidly spreading across the open source community as what appear to be aggressive AI, as 97% of their traffic originating from AI company bots.
97% are just bots trawling are just bots trawling dramatically increasing bandwidth costs, service instability and burdening already stretched-thin maintainers. Kevin Fenzi, a member of the Fedora Pogger project's sysadmin team, reported on his blog that the project had to block all traffic from Brazil. After repeated attempts to mitigate bot traffic failed, gnome GitLab implemented IOSO's Anubis system requiring browsers to solve computational puzzles before accessing content. Gnome sysadmin Bart Piotrowski shared on Mastodon that only about 3.2% of requests that's 2,690 requests out of 84,056, passed their challenge system, suggesting the vast majority of traffic was automated. The vast majority of traffic was automated. Kde's GitLab infrastructure was temporarily knocked offline by crawler traffic originating from Alibaba IP ranges, according to Libre News, citing a KDE development chat.
While Anubis has proven effective at filtering out bot traffic, it comes with drawbacks for legitimate users. Naturally, when many people access the same link simultaneously, such as when a GitLab link is shared in a chat room, site visitors can face significant delays, so something triggers that challenge, like when there's enough repeated access to a link that suddenly switches on the challenge, which is not always on there all the time otherwise. So, they said. Some mobile users have reported waiting up to two minutes for the proof-of-work challenge to complete. According to the news outlet, the situation isn't exactly new. In December, dennis Schubert, who maintains infrastructure for the Diaspora Social Network, described the situation as literally a DDoS on the entire Internet After discovering that AI companies accounted for 70% of all web requests to their services. The costs are both technical and financial. The Read the Docs project reported that blocking AI crawlers immediately decreased. Blocking AI crawlers immediately decreased their traffic by 75 percent, going from 800 gigabytes per day to 200 gigabytes per day. This change saved the project approximately $1,500 per month in bandwidth costs. According to their blog post, ai crawlers need to be more respectful. The situation has created a tough challenge for open source projects, which rely on public collaboration and typically operate with limited resources compared to commercial entities.
Many maintainers have reported that AI crawlers deliberately circumvent standard blocking measures, ignoring robots, dot text directives, spoofing user agent strings and rotating IP addresses to avoid detection. As Libre News reported, martin Owens from the Inkscape project noted on Mastodon that their problem problems weren't just from the usual Chinese DDoS from last year, but from a pile of companies that started ignoring our spider configuration and started spoofing their browser info. Owens added I now have a prodigious block list. If you happen to work for a big company doing AI, you may not get our website anymore, our website anymore. On Hacker News commenters meaning a false positive, I mean actually a true positive detect on a large company's IP address block because they just had to shut down all access to that company, to their site, because their block list has become so large. On Hacker News because their block list has become so large.
On Hacker News, commenters and threads about the Libre News post last week and a post on IASO's battles in January express deep frustration with what they view as AI companies' predatory behavior toward open-source infrastructure. While these companies come from forum posts rather than official statements, they represent a common sentiment among developers. As one Hacker News user put it, ai firms are operating from a position that quote goodwill is irrelevant unquote with their hundred billion dollar pile of capital. The discussions depict a battle between smaller AI startups that have worked collaboratively with affected projects and larger corporations that have been unresponsive, despite allegedly forcing thousands of dollars in bandwidth costs on open source. Project maintainers often hit expensive endpoints like Git, blame and log pages, placing additional strain on already limited resources, and by that they're talking about by an expensive endpoint is some page which requires a lot of database access or back-end work in order to produce the page, and so if the robot just hits that continuously, it's very resource expensive in terms of computation and access resources. Drew DeVault, founder of SourceHunt, reported on his blog that the crawlers access every page of every Git log and every commit in your repository, making the attacks particularly burdensome for code repositories. The problem extends beyond infrastructure strain. As Libre News points out, some open-source projects began receiving AI-generated bug reports as early as December 2023, first reported by Daniel Stenberg of the Curl Project on his blog in a post from January 2024. These reports appear legitimate at first glance, but contain fabricated vulnerabilities, wasting valuable developer time right, you know, to track them down and realize this isn't. This is what is this? This is not an actual vulnerability.
Ai companies have a history of taking without asking. Before the mainstream breakout of AI image generators and chat, gpt attracted attention to the practice. In 2022, the machine learning field regularly compiled data sets with little regard to ownership. While many AI companies engage in web crawling, the sources suggest varying levels of responsibility and impact. Dennis Schubert's analysis of Diaspora's traffic logs showed that approximately one-fourth of its web traffic came from bots with an open AI user agent, while Amazon accounted for 15% and Anthropic for 4.3%.
The crawlers' behavior suggests different possible motivations. Some may be collecting training data to build or refine large language models, while others could be executing real-time searches when users ask AI assistants for information. The frequency of these crawls is particularly telling. Schubert observed that AI crawlers don't just crawl a page once and then move on. Oh no, they come back every six hours. Because why not? This pattern suggests ongoing data collection rather than one-time training exercises, potentially indicating that companies are using these crawls to keep their model knowledges current.
Some companies appear more aggressive than others. Kde's sysadmin team reported that crawlers from Alibaba IP ranges were responsible for temporarily knocking their GitLab offline. Meanwhile, ioso's troubles came from Amazon's crawler. A member of KDE's sysadmin team told Libre News that Western LLM operators like OpenAI and Anthropic were at least setting proper user-agent strings, which theoretically allows websites to block them. While some Chinese AI companies were reportedly more deceptive in their approaches, it remains unclear why these companies don't adopt more collaborative approaches and, at a minimum rate, limit their data harvesting runs so they don't overwhelm source websites. Amazon, openai, anthropic and Meta did not immediately respond to requests for comment, but we will update this page if they reply.
In response to these attacks, new defensive tools have emerged to protect websites from unwanted AI crawlers. As ours reported in January, an anonymous creator, identified only as Aaron, designed a tool called Nephentes to trap crawlers in endless mazes of fake content. To trap crawlers in endless mazes of fake content. Aaron explicitly describes it as aggressive malware intended to waste AI companies' resources and potentially poison their training data. Quote anytime one of these crawlers pulls from my tar pit, crawlers pulls from my tar pit. It's resources they've consumed and will have to pay hard cash for, aaron explained to ours. Quote it effectively raises their costs and, seeing how none of them have turned a profit yet, that's a big problem for them.
On Friday, cloudflare announced the AI Labyrinth, a similar but more commercially polished approach. Unlike Nepthentes, which is designed as an offensive weapon against AI companies, cloudflare positions its tool as a legitimate security feature to protect website owners from unauthorized scraping. Unauthorized scraping, cloudflare explained in its announcement. Quote when we detect unauthorized crawling, rather than blocking the request, we will link to a series of AI-generated pages that are convincing enough to entice a crawler to traverse them. Okay, I'm not quite sure how that's that different from Nepthentes. Cloudflare reported that AI crawlers generate over 50 billion requests wow to their network. Daily, ai crawlers generate over 50 billion requests to their network daily, accounting for nearly 1% of all web traffic. They process, which says they're handling what? 5,000 billion requests? Yeah, 5,000. So 5,000.
Yeah, 5 trillion. 5 trillion requests per day Wow, Cloudflare. Yeah, 5 trillion. 5 trillion requests per day Wow, Cloudflare. The community is also developing collaborative tools to help protect against these crawlers. The AIrobotstxt project offers an open list of web crawlers associated with AI companies and provides pre-made robotstxt files that implement the robots exclusion protocol.
1:23:50 - Leo Laporte
Yeah, they should honor those. That's the key, right?
1:23:53 - Steve Gibson
Yeah, yes exactly, as well as htaccess files that return error pages when detecting AI crawler requests. As it currently stands, both the rapid growth of AI-generated content, overwhelming online spaces and aggressive web crawling practices by AI firms threaten the sustainability of essential online resources. The current approach taken by some large AI companies, extracting vast amounts of data from open source projects without clear consent or compensation and, I would add, deliberately ignoring their clearly established standards for saying please don't risks severely damaging the very digital ecosystem on which these AI models depend.
And finally, they wrote responsible data collection may be achievable if AI firms collaborate directly with the affected communities. However, prominent industry players have shown little incentive to adopt more cooperative practices, to adopt more cooperative practices Without meaningful regulation or self-restraint by AI firms. The arms race between data-hungry bots and those attempting to defend open-source infrastructure seems likely to escalate further, potentially deepening the crisis for the digital ecosystem that underpins the modern internet.
1:25:23 - Leo Laporte
Yeah, yeah. If they don't honor robots, honor robots text, then anything you do to them is fine right if they're, if they're exactly, if they're deliberate.
1:25:30 - Steve Gibson
That's a very good point, leo. If, if you know we, we might say, hey, it's kind of foul play sending them into an ai driven tar pit.
1:25:39 - Leo Laporte
But if you first said don't go in here, right because of what's in the robottxt and I presume that do cloudflare does do that yes yes, by the way, nepenthes is funny, so cloudflare calls it a tar pit. But a nepenthes is a pitcher plant.
1:25:56 - Steve Gibson
It's the plant that traps, oh right that, that, that that like it's not a fly trap.
1:26:02 - Leo Laporte
It's a pitcher, it, it has dew in it and the bugs move into it, and then, of course, it eats them. So it's just like a tarp, but it's a plant very nice from the plant kingdom of a tarp, it, I think that's very funny, yeah, uh you want to take a break?
yes, it is time I suspected you you might. I will wet my, wet your whistle while I show people the coolest thing on the internet today, our sponsor, thinkst, creates this. It looks like an external hard drive, doesn't it? With a simple power cable and an Ethernet connection. But no, no, this is the famous Thinkst Canary apot. And man, I love this thing. Let me just show you the canary interface. Huh, you love this. Thinkst, this thinkst.
Yes, this isn't a penty of its own right, it is a honeypot. In my case, I've set mine up to look like a Windows 2019 server office file share, right, but you can set it up to be any number of things whatever you want. You choose the personality, everything from IIS to a Linux database, a Mac OS X file share. You can even make it SCADA devices. Look, I could turn it into a Hirschman RS-20 industrial switch or a Rockwell automation PLC, the idea being it looks like in every aspect including, by the way, the MAC address the real thing. But when a bad guy or a malicious insider hits it, you get an alert, and no false alerts, just the alerts that matter. See, of course, of course, nowadays, modern security. You've got perimeter protection, but you may not know if somebody has penetrated your network. Right, and the worst thing is it takes, on average, 91 days before a company that has been breached realizes there's somebody inside the network. Not with the thinks canary. That honeypot doesn't look vulnerable, it looks valuable. They cannot resist it. So the minute somebody hits your canary token, those tripwires or your thinks canary, you will get an alert the alerts that matter and you can get it any way. You want sms, you can get it by Slack, whatsapp. They support webhooks, they have an API syslog, of course, so you'll always be able to get those alerts in any way that's convenient for you. Just do what I did Go into your console, choose a profile for your Canary device, you register it for monitoring and notifications and then you sit back, you relax. As long as you hear nothing, you're good. But as soon as an attacker breaches your network or a malicious insider, they'll make themselves known. They can't help themselves by accessing those Canary tokens or that thing's Canary.
I think every business should have at least one. Big banks might have hundreds, medium-sized businesses just a handful. Let me give you a pricing example. Visit canarytoolstwit. That's the website, canarytoolstwit $7,500 a year. You're going to get five things to Canary's. That's nice because you can spread them around. You can infinite number of tokens as well, so you really can lock things down. You'll also get your own hosted console. You get upgrades, you get support, you get maintenance all for the same price.
If you use the code TWIT in the how Do you Hear About Us box, you're going to get 10% off, and not just for your first year subscription, for life 10% off. Oh and, if there's any concern, if you say, well, it seems like a good idea, but really do it, you can always return your Thinks Canaries. They have a two-month, 60-day money-back guarantee for a full refund. I should mention, though, that during the entire eight years we've been doing these ads and the eight years I've been using my Thinks Canary, not one person has asked for a refund. The guarantee has never been claimed. You know why. You realize, once you got them, how did I live without them? Visit canarytools, slash twit. Don't forget to put twit in the how did you hear about us box. Find out more. Visit canarytools, slash twit, and don't forget to put twit in the how did you hear about us box for 10% off or life.
I love this thing. It's so cool, just to have it on my desk. Nobody's ever going to hack my network Famous last words but it's just nice to know. If they do, they're going to open that employee's information spreadsheet and they're going to announce themselves. I'm going to know they've been in here. All right back to you, mr G. So if you're attempting to install Windows 11, I'm going to know if they've been in here.
1:30:46 - Steve Gibson
All right back to you, mr G. So if you're attempting to install Windows 11 on a machine using only a local account without signing into Microsoft and you're wondering why doing so appears to become more difficult or obscure, it could be because Microsoft now intends to make that completely impossible. In their recent announcement of Windows 11 Insider Preview, build 26200.5516 for the Dev Channel, toward the end of a long list of tweaks and changes that they've made under the section other, microsoft wrote and I love the way they phrase this we're removing the bypass NRO dot CMD script from the build to enhance security and user experience of Windows 11,. This change ensures that all users exit via all users exit setup with internet connectivity and a Microsoft account. So, okay, it's unclear to me how forcing either Internet connectivity or being logged into a Microsoft account enhances either a user's security or their convenience or experience. But that's you know what will henceforth be required for all users setting up Windows 11. And I don't make me, I don't mean to make a bigger deal out of this than it is.
I imagine that anyone setting up Windows 11 will have already made whatever adjustments to their thinking and expectations may be required, but it is a change that I wanted to let our listeners know about. Some of the reporting I saw about this phrased it a little differently. They said, quote Microsoft has been trying to force Windows 11 users to install the OS with a Microsoft account for years, but this marks the first time when the company has made it a public policy in one of its blocks. So anyway, having shared all that, I won't be surprised if there isn't soon a workaround for this. We've seen those before when this has sort of been there.
1:33:06 - Leo Laporte
It's actually a little more. It's simpler than this, and we talked about this on Windows Weekly, which is how I know. That was a script, a PowerShell script, which actually maybe not even a PowerShell script. It was a shell script that launched a series of commands. Those commands are still there, and so what Microsoft has done is make it so that somebody who is non-sophisticated won't have a simple oh, just click this and it'll run the bypass NRO script, but all of the commands that do bypass the Microsoft login are still there. They have not removed those.
So Paul's position on this is you still can set up Windows 11 without a Microsoft account, but you need to be a little more sophisticated than you used to be, and that's Microsoft's intent because, for instance, if you're using Windows Home, it turns on BitLocker, but only if you turn on your Microsoft account, because you need a way to store that certificate. So many people lose their certificates, so microsoft's airing for the, I think this is. I've always said this is the ideal solution, which is and apple does this too you kind of have a way around it.
Yeah, by default you make it more secure but less flexible.
But if you're in the know, if you're a sophisticated user, there are ways to disable it, so they took it out of the gui that basically that little skip for now, or or or local account that they used to have right but if you paul says, and at least for now, uh, and he believes this will continue, it is absolutely possible to do this. You just don't have that script to do it anymore. Well, if you looked in the, if you looked in bypass nrocmd, you could see the, the commands. It was just well. And it would seem to me that even if you looked in BypassNROcmd you could see the commands.
1:34:46 - Steve Gibson
It was just a list, well, and it would seem to me that even if you, they wouldn't remove the ability to have a local account. So even if you had to temporarily create a Microsoft account to get installed, then you add a local account and delete the Microsoft account.
1:35:03 - Leo Laporte
That's what Paul's recommended workaround is.
1:35:07 - Steve Gibson
You know you can make a dummy Microsoft account that you don't use Right just to get you installed Exactly, and then yeah, and they can't get rid of that.
1:35:14 - Leo Laporte
You know, as long as there is a local login at some point, yeah Right. So I think it's not just as you say. You say that you wouldn't be surprised if there's a workaround. There are, there is, basically, and they're never.
1:35:26 - Steve Gibson
They didn't get rid of that yeah, okay yeah, well and again, as I said, I don't mean to make a big deal about it. Uh, you know if it's just annoying to be constantly asked if you want it. You haven't backed up your drive. Yeah, it's like hey, I've got my own backup. I, you know, there's no way to tell it to shut up, it's not for you.
1:35:46 - Leo Laporte
It's for normal users. That's the problem and it's always been the challenge in technology to make it reliable and safe for normal people, but to give we hardcore users the power that we really want and deserve.
1:36:01 - Steve Gibson
Yeah, okay, so I love this. Want and deserve yeah, okay, so I love this. Last week, google announced and unveiled what they called end-to-end encryption for corporate users of Gmail. But boy is it funky. It does encrypt a message in the sender's web browser, where it remains encrypted until it's opened in the recipient's web browser, where it's then decrypted. So technically, yeah, end to end. But otherwise Google jumped through some weird hoops to offer this. Okay.
Now, since the technology is interesting and since it might well be of interest to our listeners, whose corporations might find value here because, I mean, it's not nothing, it's just not really what we're used to I want to take us into the details, and for that Ars Technicus, dan Gooden, did a terrific job of setting this up, creating the appropriate context and explaining what goes on. R's headline last week about this was Gmail unveils end-to-end encrypted messages. Only thing is it's not true end-to-end, and their tagline was yes, encryption slash. Decryption occurs on end-user devices, but there's a catch. So Dan opens by saying when Google announced Tuesday that end-to-end encrypted messages were coming to Gmail for business users, some people balked, noting that it wasn't true end-to-end encryption, as the term is known in privacy and security circles. Others wondered precisely how it works under the hood. Here's a description of what the new service does and doesn't do, as well as some of the basic security that underpins it. Now I'm going to interrupt here just for a moment to note that the way the conventional end-to-end encryption operates is pretty straightforward. So let me set that context first, because he doesn't do that.
Each party, as we know, has a public key pair consisting of a public key and a private key, and the public keys are published in some way. So when Alice wishes to send an encrypted message to Bob, she first creates a high entropy secret symmetric key which will be used to encrypt the message and anything she wants. That's the so-called bulk encryption key, and that's just. Randomly she creates a high entropy, random secret symmetric key which she uses to encrypt her stuff. She uses that symmetric key to encrypt everything that she wishes to send to Bob. Next, alice encrypts that secret key twice, first with her private key, then a second time with Bob's the recipient's public key. She then packages the encrypted message up along with the result of the double key encryption and sends that package to Bob.
Upon receiving Alice's package, Bob first decrypts the double encrypted key using his secret key, which undoes the second encryption that Alice put on, which used Bob's private key, and, of course, only Bob knows his private key. He then looks up Alice's publicly published public key and uses it to decrypt the result of the first decryption. And the beauty of this is that only if all four of these keys were correct will Bob now have recovered the properly decrypted secret symmetric key, which he can then use to decrypt the package that Alice prepared for him, that Alice prepared for him. Now, the elegant beauty of this simple system is that Alice wishes to send something that only Bob can decrypt, and Bob wants to know that whatever he received was truly sent by Alice, since both parties' private keys must be used and only each party knows their own private key. Not only do we get strong encryption protection from anyone attempting to intercept that communication, but Alice knows that only Bob can decrypt what she encrypted, can decrypt what she encrypted, and Bob knows that only Alice can have sent what he decrypted as having come from her.
So that's true end-to-end encryption. That's not what we got from Google in Gmail, okay, so Dan explains what we did get. He wrote when Google uses the term end-to-end encryption. In this context, it means that an email is encrypted inside Chrome, firefox or just about any other browser the sender chooses as the message makes its way to its destination. It remains encrypted and cannot be decrypted until it arrives at its final destination, when it's decrypted in the recipient's browser.
The chief selling point of this new service is that it allows government agencies and the businesses that work with them to comply with a raft of security and privacy regulations and, at the same time, eliminates the massive headaches that have traditionally plagued anyone deploying such regulation-compliant email systems. So in other words, they sort of skin the cat here in a different way. They've come up with something that complies with the regulations for end-to-end encryption, yet made it much easier to deploy. Dan said up to now, the most common means has been SMIME, a standard so complex and painful that only the bravest and most well-resourced organizations tend to implement it. Smime requires each sender and receiver to have an X.509 certificate that's been issued by a certificate authority. Obtaining, distributing and managing these certificates in a secure manner takes time, money and coordination. That means that if Bob and Alice have never worked together before and an urgent or unexpected need arises for him to send Alice an encrypted message promptly, they're out of luck until an admin applies for a certificate and sees that it's installed on Alice's machine. So much for flexibility and agility.
Google says that end-to-end encryption Gmail abstracts away this complexity. Instead, bob drafts an email to Alice, clicks a button that turns on the feature and hits send. Bob's browser encrypts the message and sends it to Alice. The message decrypts only after it arrives in Alice's browser and she authenticates herself. Okay. To make this happen, bob's organization deploys what Google calls a lightweight key server, known as a KACL, short for Key Access Control List. This server, which can be hosted on-premises or most cloud services, is where keys are generated and stored. When Bob sends an encrypted message, his browser connects to the key server and obtains an ephemeral symmetric encryption key. Bob's browser encrypts the message and sends it to Alice along with a reference key. Alice's browser uses the reference key to download the symmetric key from the KACL and decrypts the message. The key is then deleted, thus ephemeral.
To prevent Mallory or another adversary in the middle, mallory in the middle, from obtaining the key, alice must first authenticate herself through Octa ping or whatever other industry identity provider or IDP Bob's organization uses. So Alice must authenticate herself to Bob's organizations, uh, identity provider and Dan said if this is the first time Alice has received a message from Bob's organization, she'll first have to prove to the IDP that she has control of her email address. If Alice plans to receive encrypted emails from Bob's organization in the future, alice sets up an account that can be used going forward. Bob's organization can add an additional layer of protection by requiring Alice to already have an account on the IDP and authenticate herself through it. Workspace product manager told ours quote the idea is that no matter what, at no time and in no way does Gmail ever have the real key Never. And we never have the decrypted content. It's only happening on that user's device. Unquote.
Okay, now I'm going to interrupt here again to note that in no way is any web browser a safe place to decrypt super secure, you know, like national security level or extremely proprietary corporate material. You know this is like in the same way when we were talking about SignalGate, as it's now being called, of, you know, national security level secrets being transacted on people's individual smartphones. It's not Signal that had a problem, because it's true end-to-end encryption. It's that it's on the smartphone device. It is decrypted after it arrives. So we have the same problem with a web browser. Right, you still have JavaScript or WebAssembly running in a web browser which is as authentically secure as we've been able to make them, but they're still being updated to cure serious, often zero-day style security vulnerabilities. That's still happening.
If you really need to send something securely, my advice would be encrypt it offline, away from any web browser. Then send it in the clear through any email system, doesn't matter, because it's been. You know it's Pi pre-internet encryption, pre-web browser encryption. You know I'm not intending to take anything away from Google. The system they've created is an interesting hack, but a hack it is, and it also represents a security trade-off for convenience, since it's running in the largest attack surface, which is today's web browser that any computer system has today. Dan finishes description by writing has today. Dan finishes description by writing.
Now, as to whether this constitutes true end-to-end encryption, it likely doesn't, at least under stricter definitions that are commonly used To purists. End-to-end encryption means that only the sender and the recipient have the means necessary to encrypt and decrypt the message. That's not the case here, since the people inside Bob's organization who deployed and manage the KACL have true custody of the key, in other words, the actual encryption and decryption process occurs on the end-user devices, not on the organization's server or anywhere else in between. That's the part that Google says is end-to-end encryption. The keys, however, are managed by Bob's organization. Admins with full access can snoop on the communications at any time.
The mechanism making all of this possible is what Google calls CSE, short for Client-Side Encryption. It provides a simple programming interface that streamlines the process. Until now, cse worked only with SMIME. What's new here is a mechanism for securely sharing a symmetric key between Bob's organization and Alice or anyone else Bob wants to email. The new feature is of potential value to organizations that must comply with onerous regulations mandating end-to-end encryption. It most definitely is not suitable for consumers or anyone who wants sole control over the messages they send. Privacy advocates take note.
So anyway, if anyone was wondering, you know heard about Google's. You know end-to-end encryption. Now we have some context. It's certainly better than what they had before. If your organization wants to use it, then you know it does keep things encrypted. But you know, if you're using Gmail in your browser, you have an HTTPS connection to Gmail, right, and anything that goes gmail to gmail remains yeah it's never been in the clear at any point right so I think this is this is really for businesses that don't want to give up full uh encryption right, because they want to make sure that they can monitor your emails in fact they may have
a regulatory requirement I think it's an interesting regulatory hack.
1:51:04 - Leo Laporte
Yeah.
1:51:04 - Steve Gibson
I think that's it. I think it's a. You know, it's like Google was under some pressure to come up with a way for people for regulations that require end-to-end encryption, like the letter of the law that it's encrypted on your device, decrypted on the recipient's device, and Google said, oh yeah, we can do that.
1:51:26 - Leo Laporte
Did you ever wonder who Bob and Alice are?
1:51:30 - Steve Gibson
I do, and boy, they have some longevity.
1:51:35 - Leo Laporte
Sometimes there is a Ted and a Carol that gets involved in these conversations and it all comes from a 1969 movie about wife swapping called Bob and Carol and Ted and Alice. You remember that right.
1:51:46 - Steve Gibson
Yeah, we're older. Yeah, us oldsters know where that came from.
1:51:50 - Leo Laporte
It's pretty funny and I would imagine people listening who don't know that are going. Who are these Bob and Alice that everybody's always talking about when it comes to encryption? I think that's where it came from. It seems like a coincidence.
1:52:01 - Steve Gibson
If it didn't, must be and it has the advantage of having a, b and c, alice, bob and carol yeah, ted, we just could throw out, we yeah ted, you know he't fit. And then Mallory as Mallory in the Middle. Oh, there you go. Mallory is also the name used for your attacker, for man in the Middle, for man in the Middle.
1:52:23 - Leo Laporte
Oh nice, that's nice, do you? Want to pause or do you want to keep going?
1:52:29 - Steve Gibson
I got a little bit more and then we got some. Oh yeah, one more and then feedback when we will pause. Okay, but this is an important one for anyone who is running Apache Parquet, a CVSS 10.0, which we know is very difficult to achieve. It's like the Olympics of bad vulnerabilities bad vulnerabilities. Apache recently received the much dreaded full CVSS 10.0 with a widely used module known as Apache Parquet, who's dispelled P-A-R-Q-U-E-T? Apache Parquet is an open source columnar as in. Instead of rows, it's columns, so columnar storage format designed for more efficient data processing. Unlike row-based formats such as CSV, parquet stores data by columns, which makes it faster and more space-efficient for analytical workloads. It's widely adopted across the data engineering and analytics ecosystem, including big data platforms like Hadoop, aws, amazon, google, azure, cloud Services, data Lakes and ETL tools. Some large companies that use Parquet include Netflix, uber, airbnb and LinkedIn. Parquet include netflix, uber, airbnb and linkedin, and now a new low complexity remote code execution. Vulnerability has been identified in all current versions of the apache parquet system.
1:54:13 - Leo Laporte
yeah, how widespread is parquet use. Is it a pretty popular?
1:54:17 - Steve Gibson
Among those who use it, I mean Netflix.
1:54:20 - Leo Laporte
Uber, airbnb, linkedin. I mean.
1:54:23 - Steve Gibson
Hadoop AWS.
1:54:24 - Leo Laporte
Amazon Google Azure cloud services.
1:54:28 - Steve Gibson
So yeah, it's got some wings there. Unfortunately, the problem was disclosed on April 1st, but since this is no joke and it would be horrible for those affected if they thought it was, I hope no one dismissed it as an April Fool's event. This maximum severity remote code execution problem impacts all versions of Parquet up to and including 1.15.0. The problem stems from the de-. Here it is the deserialization We've talked about deserialization flaws because they're tough of untrusted data. And of course, deserialization is also known as interpretation, and we know how hard it is to do interpretation correctly. It could allow attackers with specially crafted Parquet files to gain total control of target systems, exfiltrate or modify data, disrupt services or introduce dangerous payloads such as ransomware. The vulnerability is tracked as CVE-2025-30065 and, as I said, carries a CVSS-V4 score of 10.0. It was fixed with the release of Apache version 1.15.1. So it is some solace that in order to exploit this flaw, threat actors must convince someone to import a specially crafted Parquet file for Parquet to then deserialize. But we all know that social engineering attacks remain some of the hardest to defeat and it might well be that there are other vectors. So anyway, I wanted to put it on everyone's radar.
If you happen to know that you're using Parquet or know someone that does. The good news is it has not been publicly leveraged. It's not known to be used. It was discovered by Amazon AWS security folks. They told Apache because AWS uses it. They told Apache, apache's updated it. It see what's changed. Reverse engineer the exploit and then go looking for publicly exposed Parquet instances. So if you're using Parquet, update immediately because you want to beat the bad guys to it. And now, leo, let's take a break.
1:57:15 - Leo Laporte
Oh, I thought you wanted me to say butter. Okay, butter, butter Parquet.
Parquet, parquet let's take a break. Oh, I thought you wanted me to say butter. Okay, butter, butter, parquet, I'm just teasing. Uh, a little break here, we will get back to the action. Don't worry. Our, our feedback section is coming up next.
But first a word from steve, my favorite password manager. Everybody ought to be using it. You're all using. You all use a password manager, of course you do. Does your business? Does your business use one you like to use? Do your friends and family?
They all need to know about bit warden, the trusted leader in passwords, yes, but also secrets, really handy if. Have you ever come on a minute, tell the truth committed a api key to your github? You have. Who hasn't? You'll want to know about secrets, passkey management too. Bitwarden is absolutely great for passkeys. It's what I use for all my passkeys. It's fantastic. With more than 10 million users over 180 countries, 50,000 business customers worldwide, that kind of surprised me. It's a very popular enterprise solution too, consistently ranked number one in user satisfaction by G2, recognized as a leader in software reviews, data quadrant, bitwarden protects businesses worldwide and, by the way, because it's easy to use, it's simple, it's clean, it's efficient, it makes the IT department happy because it's truly secure. It makes users happy because they can use it.
Now you'll love Bitwarden Send. This is a tax time right. If you're sending information to your tax preparer or they're sending your returns back, I hope you're not just sending an email. I hope you're not using quote end-to-end encrypted Gmail. You need Bitwarden Send. Real end-to-end encryption ensures your forms remain protected. And here's the best part your tax preparer doesn't need an account to access it. Just one side of the transaction needs to have a Bitwarden account. So I think that's fantastic. A great way to send private information to anybody. You'll avoid risky email attachments. You'll share confidential documents with password protection. But there's more. There's expiration dates, there's view limits. You get full control over who accesses your sensitive information and how.
Let's talk passwords in the enterprise. New findings from Bitwarden highlight that 65% of enterprises much more than half, the majority of enterprises still rely solely on passwords. We know I mean. Passwords are fine, but there are better ways. Password management is cited as the top IAM challenge for 35% of organizations. Only 21% implement passwordless authentication, which means you're facing ongoing credential security risks. Just the last show I accidentally showed my password on the air right, but I didn't worry. I didn't worry because I got Bitwarden Bitwarden Office Enterprise Essential Tools with end-to-end encryption. We just talked about that MFA, secure password sharing.
Don't write a password on a post-it and give it to your co-worker Use Bitwarden. It also addresses all the current and many future authentication needs. They just announced they're ISO 27001-2022 certified. That's the, of course, internationally recognized standard that assures enterprises, developers and security teams that Bitwarden meets stringent security and compliance requirements. This complements their existing compliance with SOC 2, type 2, gdpr, hipaa, california's CCPA. This just really reinforces that. Bitwarden is your trusted partner for security in enterprises. And again, it's easy to use, because it's no good having a security solution that is too hard for people to use. They'll just go around it.
Bitwarden's setup only takes a few minutes. They support importing from most password management solutions, so it's an easy move. And, of course, it's open source, which is great. If you're curious, you can inspect their source code Anyone can. It's regularly audited by third-party experts.
Look, you and your business deserve an effective solution for enhanced online security, and you know what. So do your friends and family members, who are still writing things on Post-it notes or using the same password on multiple sites. What a calamity it would have been had I accidentally revealed a password that I used on many, many sites earlier today. No, because I use unique passwords everywhere. All I had to do was fix it on that one site and I'm done. Get started today with Bitwarden's free trial of a Teams or enterprise plan. Or if you're an individual or you know an individual who needs Bitwarden's free trial of a Teams or Enterprise plan, or if you're an individual or you know an individual who needs Bitwarden, tell them free forever.
Unlimited devices, unlimited passwords. Pass keys yes. Yubikeys and other hardware keys yes, for individual users. Individual users even can store their own vault if they want really truly trust no one. Bitwardencom slash twit Please use that address so they know. You saw it here. Steve converted to it. I converted to it a few years ago. I could not be happier. Bitwardencom slash twit Great sponsor, great product that almost all of us use. I think at this point it's a great one.
2:02:39 - Steve Gibson
All right back to Steve so at Techno Agorist, so this must have been through X where I checked in. He wrote regarding Neil Asher's novels. They may not be on Kindle Unlimited, but I found them at my local library. Nice that I've been reading them, thanks for the recommendation and I appreciated uh being able to share a reminder about printed books and that's wrong with them yeah, I'm, uh, I'm still enjoying neil.
I'm on book number four of the first five-book Agent Cormac series, as it's called, and I'm having a great time. The books are long and involved. The style Neil uses, for the first three at least, was—and I guess it's to a lesser degree now in number four— was to create several parallel plot lines that initially don't appear to bear any connection to each other. There's no obvious relationship, so you'd sort of move around between them and you're thinking, okay, why do I care about this person? But uh, you know, as the story progresses, they eventually converge and, uh, you end up. I remember at one point thinking I'm having a lot of fun with this book.
So anyway, uh, thank you for uh techno agorist for uh your note about uh. Books are still available from libraries. Uh in print amazing.
2:04:10 - Leo Laporte
That's certainly a way to get a thunk it, I wouldn't occur to me.
2:04:14 - Steve Gibson
Uh, eric's, uh sidell said Steve, I just listened to part of your podcast and it was funny that you mentioned something that happened exactly to me as well In the past couple of days. I had Microsoft two factor authentication reset requests show up in my email and then happened to look in my sign in activity activity and it is a sign-in request every minute to my account. It's just insane. Make sure you have your two-factor authentication turned on. Holy smokes. And I put in the show notes just a snapshot that he had sent me. That does you know? Indeed, show, in fact, sign--ons every minute, or several times in the same minute. So again, the idea that some guy or the bots apparently are just sitting here pounding on people's email without better protection is it is really disturbing.
Matthew West said hi, love the show. I bought a used Fitbit with a cracked screen. I forgot that I would need the pin shown on the screen in order to pair it. I'm trying to pair by constantly changing one time, the constantly changing one time code, in the hopes it eventually works. In other words, he's guessing. Oh, forget about it. He said this made me wonder what the best strategy is and how many attempts would be needed to reach a 50% chance. Sorry if this was already answered. I should look through the transcripts. Thank you Well, matthew. We previously discussed this question a few months back, when we took a deep dive into the precise operation of hash-based one-time passwords. That podcast was 1009, and we received an unusual amount of positive feedback from our listeners who enjoyed thinking about the various aspects of a six-digit code that was changing randomly every 30 seconds.
The answer to the first part of your question, matthew what's the best strategy is that, since the proper PIN code at any given instant is completely random, there can be no best strategy, since no guess can by definition be any better than any other. So if patience could be considered a strategy, then patience would be the best strategy, because a great deal of that is going to be necessary. So exactly how much? The second part of your question asked how many attempts would be needed to reach a 50% chance, and that is something that's knowable. At the bottom of page 21 of episode 1009 show notes, I wrote the probability of things happening is something that often trips people up. If the probability of something random happening is one in a million and that is the case of the probability of a correct guess, is one in a million since it's of a correct guess, is one in a million since it's from 0, 0, 0, 0, 0, 0 to 9, 9, 9, 9, 9, that's a million possible combinations, we might tend to assume that giving that one in a million thing one million opportunities to occur, or, in our case, one million guesses, we would probably obtain a collision of six-digit values, and that's true, but it's not guaranteed. Probability theory tells us that, even given one million guesses of a one-in-a-million event, there's a 36.79% chance of never hitting upon the value we're seeking. But that means that, given one million guesses, there is a 63.21% chance of hitting it. So you know better than 50-50.
Okay, for random events, it's all about probabilities. And so here's the answer to your question, matthew 693,147 guesses so just shy of 700,000, would be required to hit the 50-50 point for an even chance of any of those one in a million guesses being correct. So that's why patience will be the best strategy. Maybe getting a different Fitbit would be a better idea, since you're going to be guessing, for I don't know how fast you can guess, but it's going to take just shy of 900,000 guesses to reach the 50% point. That would try my own patience. Yes, actually, if you were to walk up a step for every time you made a guess, you wouldn't need the Fitbit, because you would be fit.
2:09:35 - Leo Laporte
There you go. That's clever. Yes, you got the guess Just take the stairs.
2:09:41 - Steve Gibson
Jason wrote hi, steve and Leo. Long time listener and happy Club Twit member. Thank you, jason. He said as we all move to delete our 23andMe data. I have a maybe amusing story.
When I signed up for 23andMe years ago, I thought I would attempt to get some privacy by obscurity. I created my 23andMe account with a fake name, with a new Gmail for that fake name. My thought was, if they were ever hacked as they were or sold their data as they are, at least my DNA would not be tagged with me by name. So I also made up a fake birthday, in keeping with the obscurity strategy. Cut to this week when I went to delete my data and found that birthday is used as a form of authentication is used as a form of authentication.
I have no idea what date I gave them and I never thought to record it. I tried permutations of my own birthday until I ran out of guesses and locked myself out. Emails to their support revealed that the only way to prove my identity was to provide government-issued ID. I'm not likely to give my ID to someone actively selling all of their assets to the highest bidder anyway, but I certainly can't when no such ID exists. Oh well, guess I'll have to continue to rely on obscurity. Thanks for all you do, jason, and he put that in air quotes, so I don't think that's even his name.
2:11:18 - Leo Laporte
We don't know his name, we don't know his birthday, we don't know.
2:11:23 - Steve Gibson
I love that Jason put his name in quotes, you know, suggesting that he's quite deeply committed to remaining anonymous and obscure, as indeed he is, and given that no one knows whose DNA his is anyway, let alone who he is, I'd say there never was any need to delete it in the first place. But I understand, you know, for the sake of why not, you know, giving it a try. Anyway, he sort of locked himself out from being able to do so. An anonymous listener wanted to share some thoughts about leaving Windows. He said Hi, steve, please keep my name, company and project private because it would be easy to reverse engineer who my company is. He said I've been listening for years. Thank you for all you do. He said I've been listening for years. Thank you for all you do.
I'm a security researcher and developer at really big company X. I mostly maintain a popular open source tool name redacted With respect to moving away from Windows to an open source solution. And again, remember, really big company X. I know the name of the company and it is really big. He said with respect to moving away from Windows to an open source solution, much of my company's software, which is firmware build chain, is built upon Windows. Buildchain is built upon Windows. Microsoft is in the process of relicensing all of our server WinOS and MSSQL agreements and, as a result, our cost will be going from a per-compute device license to a per-core license. Oh boy, and I don't know about you, leo, but I got 20 cores yeah that's a massive increase.
He says, as such, the cost would be going from thousands of dollars to millions of dollars to millions of dollars. In response, we are simply moving as much of our infrastructure as we can to an open source variant. He said it seems crazy to me that M and he has that dollar sign for MS. You know, m dollar sign is so arrogant that they think there's no alternative to them, or at least that the cost would be too much for us to absorb. About that they have miscalculated. Yes, it will cost us to move, but it'll be so nice once we've done so. Now we just need to move all of our clients from windows to Linux and I'll be a happy camper. Thanks again for all you do. Slash Anon.
So this person was actually Leo, just one of many of our listeners who wrote to me in response to last week's EUOS podcast. I heard similar stories over and over and over. Microsoft apparently believes that they will be maximizing their bottom line profit by squeezing more money out of fewer customers, because the theme I kept hearing playing out over and over was that people were finally and at long last, throwing in the towel, giving up and biting the bullet to move to free and open source solutions. Those solutions have been steadily maturing through the years and are finally solid enough to be dependent upon more so than Microsoft, you know. And the message is, you know. The message was that they will be moving because Microsoft's policies appear to be predatory. Predatory was the word that several of our listeners independently used and I thought whoa so? And I suppose it makes sense. If Microsoft can increase their profit and reduce the burden of support for all those pesky customers that you know they'd rather not have, then fine.
2:15:52 - Leo Laporte
Go to.
2:15:53 - Steve Gibson
Linux People are saying okay, yeah. Tj Asher said Steve, I heard Leo mention Jackpot Junction in that list of companies on the ransomware site.
2:16:07 - Leo Laporte
Oh, yeah, yeah they were one of the hacked or ransomware companies.
2:16:10 - Steve Gibson
He said that's a casino here in Minnesota. So I went to their website and they have a big notice. It says slot machines and kiosks are currently unavailable. Bingo is canceled until further notice the special bingo. No, don't take my bingo. No, not the bingo. The special bingo session is postponed until a later date. Continuity is postponed until further notice. Promotional drawings are postponed until further notice. Dakota Dining is closed until further notice.
2:16:52 - Leo Laporte
Boy, this really hit them hard.
2:16:54 - Steve Gibson
Oh, I feel bad for them. Full deck is open for breakfast from 7 am to 11 am, with regular menu from 11 am until close. Table games and circle bar will remain open. Thank you for your patience and understanding. We will provide updates as they are available.
2:17:12 - Leo Laporte
They got hacked, all right.
2:17:13 - Steve Gibson
And TJ signed off saying definitely looks like they got hacked. Keep up the awesome work. Regards TJ. So for anyone who's interested remember I think it was what was it Last week's podcast? I think it was grcsc slash. 1019 was the shortcut that I created to take us over to Ransom List or what it was called. Oh yeah, ransomlookio. Yeah, to ransom list or what it was called. Oh yeah, ransom lookio. Yeah, grcsc slash, uh, uh 1019. And that's ransom lookio. And I mean I looked again and it's just it's hopping over there. Recent posts on on the left is is uh, takes you to the listing and yeah this is today.
2:17:57 - Leo Laporte
Yep, this is just today. These are all places that have been national association for stock car auto racing.
2:18:04 - Steve Gibson
They're gone. Third avenue management gone. Crystal hyphen dcom gone.
2:18:10 - Leo Laporte
Coop 57 gone royal saudi air forcegovsa Royal Saudi Air Force dot gov dot sa Liberty tax.
2:18:20 - Steve Gibson
They're going to be paying some tax. Yeah, cvte.
2:18:25 - Leo Laporte
This is the list you don't want to be on.
2:18:27 - Steve Gibson
Oh boy. And again, if any of our IT friends listening are having a problem with their CFOs, just say okay, c cfo, just go over here.
2:18:39 - Leo Laporte
Not one of these companies wants to be there and they didn't give their cio enough money yeah, yeah, wow this is incredible um, and it was good to have that um, confirmation that you know we saw that casino on here. Somebody listed there is sol I mean not a good thing by any means no bingo for bongo no bingo for you no.
2:19:07 - Steve Gibson
Heinrich johnson said hello. I just thought I'd clarify something you and leo said in episode 1019 about cloudflare hosting 20% of the web. The 20% figure most likely refers to sites behind Cloudflare's WAF, w-a-f, you know, web Application Firewall not actual hosting, especially since they referred to their free plan, which does not include hosting. That said, when behind a W-A-F, cloudflare does terminate TLS, which means that they are an intentional man in the middle that can see request information, including login credentials, slash Heinrich. So thank you, heinrich. So a better way to say it would be that Cloudflare is fronting for 20% of the internet's website properties. Harry Pilgrim said Steve, you and legal continue to say that you use certificates to log into SSH servers. This is not completely accurate. Ssh could be configured to use public private keys.
2:20:15 - Leo Laporte
Yeah, that's what I say. I never say certificates.
2:20:18 - Steve Gibson
Okay, then it's I who am saying certificate, but these are not certificates.
2:20:21 - Leo Laporte
No.
2:20:22 - Steve Gibson
A certificate is composed of uniquely identifying information. Blah, blah, blah. He explains that. So thank you, harry, for correcting us. I certainly stand corrected, but this gives me the opportunity to mention my absolute favorite SSH client and server solution for Windows-centric users, which is Bitvise B-I-T-V-I-S-E dot com. They're not a new discovery of mine, because I would never recommend something like an SSH client and server without first obtaining sufficient experience for any such recommendation. I've now been using their solutions since 2018, so I've gained seven years of experience with their software and their company and I cannot recommend them more highly. And I cannot recommend them more highly.
If all you need is an incredibly good SSH client for Windows for accessing remote SSH servers, you can use theirs free of charge. The BitFi's client is free. If you want a matching terrific SSH server for Windows, you can take theirs out for a 30-day spin for free, after which a one-year license is $100. But only the access to upgrades expires after a year. That server software will run forever. After a year, that server software will run forever. Mine's expired a few times and they've had some updates and I've thought okay, I should re-up because I'm using their server very happily. I've been with them for seven years, I can attest that they are not constantly fixing mistakes. Only very occasionally do they have something that they need to tweak, and normally it's for some edge case. That doesn't affect me, but I want to stay current with them anyway. I could not be more pleased with them and I cannot imagine ever having a need to switch. So just for the record, bit vice b-i-t-v-i-s-e is my ssh solution for windows that's one of the main reasons I'm not a windows user.
2:22:37 - Leo Laporte
Is I need a command line, uh, that I can do things like that. I should say like this and log in to a remote server, uh, I like having a command line, I, I like it too it is. It's a good thing does but bit, so I always for a long time. I mean, I haven't used windows in a while, but I used Cygwin. Is that like all done? Is that old hat C-Y-G-W-I-N? Maybe it is. The device looks pretty nice.
2:23:07 - Steve Gibson
It's really nice. I mean it manages our public and private keys, synthesizes keys. The server tells you it's never seen this key before. It tries multiple styles of authentication in sequence uh, you're able to maintain a list of previous ssh servers and select. It'll bring up a console window for you. So like when I log, when I, when I ssh, ssh in to my free BSD Unix, I get a console window. Or when I SSH in even into Windows, I get an admin prompt window Right right.
And I'm able to bring up a two-pane file copy so I can drag and drop files back and forth.
Anyway, it's just a great solution Good Bitvice, free, highly recommended Bitvice. David spicer said steve, I was listening to podcast episode 1019 and as you talked about troy hunt getting fished, I couldn't help but wonder how one could help prevent this type of quick acting attack. I know pass keys would solve a lot of this in the first place, but I often see cloud services that support pass keys also allow for username and password as a backup. I personally find it difficult to see how sites that support both options are safer. Of course you're singing my tune, right. I've said as long as you offer a fallback, then it's.
The email continues to be the weakest link in the past in the chain. I just logged into hover a minute ago when you were giving our first advertiser, our first sponsor, because I wanted to see how much a dot secure domain would cost, and I noted that right there under my prompt for a one-time authentication was I don't have access to my authenticator. Well, okay then how good is this? Anyway? He said my online banking site requires a one-time password code just to log in. Once, he said, I can view all of my account information normally. However, if I want to perform any money transfers, I am prompted for a new one-time code before I can do so. That made me think that this method might be useful with other online services that only support one-time password multi-factor authentication login, such as MailChimp, even after you have signed in, if you wanted to perform a security relevant action, such as exporting data which, of course, troy got bit by, which is what made David think about this changing authentication methods or viewing API keys that would require a new one-time password code from your authenticator. This would help prevent attackers who phish a login from you from being able to make changes or steal sensitive information without having to phish for a second one-time password code from you. Well, that's just my thought. Anyways, I'm glad I found your podcast nearly a decade ago. I love listening to you and Leo every week. Every episode is a good one, except today is extra good, and your tools like Spinrite, validrive and the DNS Benchmark are amazingly useful. Really looking forward to buying the pro version of the DNS Benchmark when it comes out for my lab environment. Have a great week, thanks, david. So I agree with David. Completely.
Requiring the reuse of a one-time password or OTP token before proceeding with any extra sensitive action after being logged in makes a ton of sense and think about it. It's exactly analogous to pretty much any site asking us to resupply our current password as part of the process of changing that password. Right, you know why? Process of changing that password? Right, you know why? We're obviously already logged in. In order for us to even be presented with that opportunity of changing our password, we have to be logged in with our password. The site already knows who we are enough to allow us to be roaming around inside it. So why ask us to reassert our current password before we're able to change it? Obviously because changing our password is seen as a particularly sensitive action.
But to David's point, it's interesting that this reuse of one-time passwords does not seem to have filtered down into the operation of most sites beyond login authentication, his bank and others being a common exception. And I think I know why. My presumption is that the reason for this is that most sites are still using some canned OAuth login authentication solution and have not bothered to build in one-time password reverification. Perhaps in time this will change, since reprompting for one-time passwords, I think, makes so much sense. It really ought to be done. But his point's a good one. No one's doing it. John rostern said steve, I've been a long time security now listener and I've always appreciated your insightful commentary and analysis, mixed with some humor, on all things related to cybersecurity. I was a bit taken aback, therefore, by your somewhat dismissive comments regarding the Security Technical Implementation Guides STIGs in episode 1018. The STIGs and they are at https, slash and Leo, you should go there Publiccybermil slash STIGs, he said, represent an authoritative resource for secure systems deployment. The voluminous, voluminous.
2:29:34 - Leo Laporte
Voluminous, Voluminous. There it is voluminous.
2:29:37 - Steve Gibson
Thank you, I got started off on the wrong foot yeah, you gotta start right the voluminous documentation and it is voluminous and tools are provided free of charge.
In the upper right, click on stigs um free of charge, including the security content automation protocol benchmarks. Misconfiguration has been and remains a primary threat actor and, following guidance such as that provided by the STIGs or the CIS benchmarks in the deployment process is a critical preventive control. Your show is a valuable resource for security practitioners that help evaluate the state of the practice across the community. It would be a disservice to minimize the potential value of a resource such as the DISA STIGs. Kind regards, john Roster. So thank you, john. I stand before you, willingly chastened. I stand before you willingly chastened. I did not intend to be dismissive of the Stigs because I was not at all familiar with them, but I'm always wary of just sort of generally of bureaucracy and, by extension, the trappings of bureaucracy. This is why, for example, I've been so pleasantly surprised by the value and effectiveness of CISA. I've been so pleasantly surprised by the value and effectiveness of CISA. You know value and effectiveness is never what I expect from government agencies, especially cyber agencies. So thank you for correcting me on the matter of the value of the STIGs For anyone who's interested in these security technical implementation guides. I have a link to them, which John provided in the show notes. Michael Swanson said and it appears that many of our listeners have encountered these STIGs. Michael said hi, steve.
In a recent episode Dan Linder brought security technical implementation guides, stigs, to your attention. I thought a little more info might be useful to your listeners, as STIGs are very useful in hardening systems against threat actors. These STIGs are created and maintained by the US Department of Defense in cooperation with the manufacturers and developers of various hardware and software. They are reviewed and updated continuously, with a quarterly publishing cycle. Stigs exist for a wide variety of hardware devices, most notably firewalls and network switches, operating systems Windows, macos, various Linux distros, vmware, ios, android, etc. Web browsers, chrome, firefox, etc. Common applications, ms Office, adobe, etc. Even Active Directory, one of the most important if you want to keep attackers from moving laterally in your network. As Dan mentioned, some of the settings are policy and procedure User accounts are deleted from the system when an employee leaves the organization, and so forth while others are technical Two-factor authentication is required to access the system Bottom line. These checklists of settings work.
Searching for DISA, d-i-s-a, space, stig, s-t-i-g will take your listeners to the library. Best regards Mike Swanson. So, mike, thank you. This makes absolute sense. I went over oh, I know where I was, leo. It was at stigviewercom S-T-I-G-V-I-E-W-E-Rcom slash stigs and took a look around.
There is a lot of interesting security content organized by the name of the hardware or software. That's the topic of each of the many individual security technical implementation guides. You can go to stigviewercom and then just choose Stigs in the upper that's what I was thinking of in the upper right corner, top of the screen menu, to see a huge, alphabetically sorted list of very useful security hardening checklists. I will be. My next Windows server will be I think it's Windows Server 2022, which was the latest, the last of the Windows 10 equivalents, and they have a long list of things you absolutely positively want to do. I already stumbled on one that was a little gotcha in IIS, some weird thing that was not blockable, that would allow an undocumented protocol to get through, and I thought, whoa, and it worried me, like what else is in there? So I will definitely be going through the list before I deploy Windows Server 2022. It looks like a great resource. So thank you, listeners, for not letting me just blow that off because I didn't know any better.
2:34:36 - Leo Laporte
Good, leo, yes.
2:34:37 - Steve Gibson
Let's not blow off our last please, let's not supporter, sponsor. And then we're going to talk about multi-perspective issuance, corroboration, finally, and why all certificate authorities gotta have it 20 120 episodes.
2:34:57 - Leo Laporte
We finally got around to it.
2:34:59 - Steve Gibson
Well, it didn't exist until last week, but okay, never mind our show today.
2:35:05 - Leo Laporte
Well, in that case, we're on it.
2:35:07 - Steve Gibson
We are on top of it, oh yeah breaking news we, we got you some of that multi-perspective issuance corroboration.
2:35:14 - Leo Laporte
You bet you finally, here, uh, today we are brought to you by delete me, and boy, I love delete me. We use delete me at twit because we realized that, uh, privacy is important, not just, you know, for privacy, it's important for security too, because we got spearfished and it was clear that the spearfisher knew a lot about our ceo and our employees and who reported to who and whose phone number was what, because they were able to buy that information online from data brokers. Have you ever searched for your name online? Don't. I don't recommend it. You will not like how much of your personal information is right there in public. And the worst is they say you know, for four bucks more, we'll give you the you know his prison record or whatever you know. It's like what this is, because this is a an unregulated uh sector. Uh, that is widespread. Use it. It's the data brokers of the world. They collect information, they buy it and they sell it on. They put together a dossier on you, and it's not just you.
Maintaining privacy is really an issue for your company. It's for your family too. Deleteme has personal plans, individual plans, family plans. Yes, you can ensure that everyone in your family feels safe online. Delete me reduces risk from identity theft, from cyber security threats, from harassment and more. Once we used to delete me to protect us, uh from people spear phishing our ceo. We noticed none of her information was online anymore. But you know it's so delete me's.
Experts will go out and find and remove your information from hundreds of data brokers. That's the first thing they do. It's important, though, to understand they won't stop there. Delete me will continue to scan and remove your information regularly. I'm talking addresses, photos, emails, relatives, phone numbers, social media, property value and a lot more, including, as Steve and I learned, our social security numbers. Not illegal to resell those. Anyway. If you set up the family plan, for instance, you'll have discrete controls for each member of the family, because each one might have a different privacy interest, so you get different settings, easy to use controls, and this just protects you.
As long as you're a member, they will continue to delete this stuff. It's really the only way. First of all, there's so many data brokers you couldn't possibly get to all of them, but second, there's new ones every day, literally every day, because it's a very profitable, highly legal, highly disgusting but highly legal business, and so more pop up all the time. Very lucrative. Protect yourself, reclaim your privacy. Visit, join. Delete mecom slash twit. If you use the offer code twit, you'll get 20 off. If privacy is important to you, this is a really good way to do it. Join. Delete mecom slash twit. Use the offer code twit at checkout. It worked for us. Steve now. Whatever the hell, this is multi-perspective issuance corroboration. It's time to dig into it that's right.
2:38:35 - Steve Gibson
Today's main topic was an outgrowth of an interesting change that the famous CA browser you know, cab C-A-B CA Browser Forum, just ratified. The CA Browser Forum consists of those people who determine what criteria are needed for web browser certificate issuance, how long various issued certificates will be permitted to live, how browsers will deal with certificates and everything else that's relevant surrounding the increasingly crucial need for clients on the Internet, whether they be people or automated systems, to be assured that the servers they're communicating with at the other end, somewhere else, anywhere else in the world, are really the entity they claim to be. A couple of weeks ago, the CA Browser Forum agreed to and this was a unanimous agreement, and this was a unanimous agreement agreed to significantly up the ante for all certificate authorities everywhere on one crucial aspect of the mechanism that is relied upon for verifying the ownership and control of the domains for which certificates are being issued. I first learned of this from Google's announcement of this news. Google wrote because, of course, google is an active participant in the CA browser forum thanks to Chrome and they have their own root program. They said the Chrome root program led a work team of ecosystem participants, which culminated in a CA browser forum ballot to require adoption of MPIC, which is the initials of today's podcast topic, via ballot SC-067. The ballot received unanimous support from organizations who participated in voting. Unanimous support from organizations who participated in voting Beginning March 15, 2025, so that's you know. Last month, middle of last month, cas issuing publicly trusted certificates must now rely on MPIC as part of their certificate issuance process whatever that is, of their certificate issuance process, whatever that is.
Some of these CAs are relying on the OpenMPIC project to ensure their implementations are robust and consistent with ecosystem expectations. Okay, so something recently happened in the world of web server certificate issuance. This whole area is a fascinating subject which this podcast has spent time examining through the years. So what exactly is MPIC? Here's how Google explained it, and then we're going to digress. So Google said, before issuing a certificate to a website, a certificate authority must verify the requestor legitimately controls the domain whose name will be represented in the certificate. This process is referred to as domain control validation, and there are several well-defined methods that can be used. For example, a CA can specify a random value to be placed on a website and then perform a check to verify the value's presence has been published by the certificate requester, despite the existing domain control validation requirements defined by the CA Browser Forum.
Peer-reviewed research authored by the Center for Information Technology Policy of Princeton University and others highlighted the risk of border gateway protocol attacks and prefix hijacking resulting in fraudulently issued certificates was not merely theoretical, as it was demonstrated that attackers can successfully. I'm sorry that attackers did successfully exploit this vulnerability on numerous occasions, with just one of these attacks resulting in approximately $2 million of direct losses. Okay so, multi-perspective issuance corroboration, referred to as MPIC, enhances existing domain control validation methods by reducing the likelihood geographic or routing vantage point which an adversary could influence. As demonstrated by security researchers, mpic implementations perform the same validation from multiple geographic locations and or internet service providers. This has been observed as an effective countermeasure against ethically conducted real-world BGP attacks. Okay, so let's clarify this.
In order to really understand the problem, we need to first revisit the operation of the internet at its most fundamental level. It's been a long time since we've done that, so let's first do a quick bit of review about how exactly the internet works. As we discussed way back in the dawn of this podcast, the brilliant way the internet works, and the thing that has ultimately been wholly responsible for the internet's robustness is that it has never tried to be perfect. Its original, brilliant design relied only upon a best effort packet routing system. In this system, data to be sent from point A to point B was first packetized by breaking anything larger than a packet, which is around 1500 bytes, into multiple individual packets. Each individual packet indicates where it's from and where it hopes to go. The packets are then dropped one by one onto the internet.
The internet itself, as we've come to know it, consists of a massive network of so-called big iron internet routers, each of which is connected to a bunch of its neighboring big iron internet routers, as each of these routers has multiple high bandwidth interfaces, each of which connects to other, similarly well-connected internet routers. So the internet itself is actually nothing more than a huge global quilt of large industrial strength routers, each of which is interconnected to its nearest neighbors in a huge, largely ad hoc array. The Internet's users are individually connected to one of these big local internet routers by their ISP, which then drops their packets onto the big iron router that's run by the ISP. So that's the entire structure. That's it. So upon arriving at the first internet router, that router obtains so upon a packet arriving at the first internet router. That router obtains the packet's requested destination, which of the many other big iron internet routers it should send that packet to in order to move that packet closer to its requested destination. So the packet is then forwarded to that next router which moves it closer to its intended recipient.
These individual routers have receiving buffers on their interfaces which allow incoming packets to queue up while they're waiting to be forwarded. But it might happen that too many packets arrive from too many different interfaces, all requesting to be forwarded out through the same destination interface, and that might not be physically possible. There's too much incoming all trying to go out of a narrow pipe outgoing. In that case the router's incoming packet buffers would overflow, with nowhere left to temporarily store any newly arriving packets, and those packets would be dropped and lost forever. At first this might seem like a very bad thing, like a critical flaw in the fundamental design of the system, but it turns out that this reflects the original brilliance of the internet's designers. They said, okay, no, that's not good. So let's make it okay. Let's make it survivable. Let's design the protocols that place these individually potentially lost packets onto the internet in such a way that a packet loss is okay, such a way that a packet loss is okay. So, for example, in the case of the UDP protocol being used for DNS lookup, if an answer to a query for a domain's IP address that was sent out in a UDP packet, just sort of hopefully and blindly, if it's not received within a reasonable amount of time, the query will be retried and often reissued to all the other DNS servers that the client knows about, and this will continue. The retrying will continue until it finally gives up. But a lost packet will just simply be retried. So crazy as it might seem at first, every internet protocol that generates and receives individual internet packets assumes that its packets may not arrive at the other end and arranges for that possibility.
This brilliant design decision takes the pressure off the Internet's packet delivery system, which is simply a massive ad hoc network of loosely interconnected routers. That's all. It is A whole bunch of routers all connected to each other. This allows them to do the best job they can of receiving packets on their various interfaces and sending them along their way toward their destination by routing them out of other interfaces. And if incoming packets buffers overflow, that's not the router's problem. The protocol which originally generated the packet will deal with that. Okay, so what does all this have to do with BGP? Packet will deal with that. Okay, so what does all this have to do with BGP?
This massive network of interconnected routers needs some means of knowing which IP address ranges should be sent out of which of their many interfaces. To answer this question, each router contains a routing table to specify which addresses can eventually be reached through which interface. How are these big routing tables determined and maintained? That's where the Internet's BGP, the Border Gateway Protocol, comes in. Protocol comes in. Bgp is used by the internet's big iron routers to coordinate, synchronize and update their understanding of which packets should be sent. Where An ISP's big iron internet router uses BGP to advertise the various blocks of IP addresses it has been assigned, it the ISP has been assigned by the internet's governing bodies and which its customers are busy using. Bgp sends this information to all the routers that connect to the ISP's router, so that they in turn know to forward any packets they receive on any of their other interfaces to the interface with which they connect to the ISP's router. After setting up their own routing tables appropriately, each of those routers in turn use BGP to forward their updated routing tables to all of the neighbors that they connect to, and so on and so on, and so on, until eventually every big iron router anywhere on the Internet has received the information, the propagated information, about where to send any packets that are destined for that ISP's big iron internet router.
And, believe it or not, this entire system works, and it works with astonishing reliability that we're all spoiled from now. When it fails, failures are generally local and are quickly fixable. The system is not perfect. Through the years we've covered the news of mistakes, innocent mistakes, made with the internet's big routers, which you know for a very, for example. For example, a very few hectic minutes might attempt to route all of the entire Internet's traffic through a bungalow in Myanmar. But you know, perfection is understood to be impossible. So a system that's self-healing and resilient in the face of mistakes is what we want and it's what we have today. And also through the years, the original vulnerabilities in these systems have been found, recognized, shored up and improved. So this finally brings us back to the rules change that the CA browser recently enacted.
In order for me to obtain a TLS certificate from DigiCert, my certificate authority for the GRCcom domain, I need to demonstrate that I'm in control of the GRCcom domain. So DigiCert gives me a simple file with a random gibberish name and random gibberish data content for me to place in the root directory of my web server at GRCcom. Once I've done so, I let DigiCert's automation know and it attempts to obtain that file by that name with the proper contents, from the root of GRCcom. If that can be done, that proves to DigiCert that, whoever I am, I'm able to affect the content of the website located at GRCcom, which no one else is supposed to be able to do, located at GRCcom, which no one else is supposed to be able to do, and thus I'm allowed to obtain an identity certificate which covers that domain. But here's the problem when DigiCert's automation reaches out to my ISP in Utah, which then drops them onto its big iron internet router for them to then be sent from Utah to my ISP in California and then to GRC's web server. In other words, digicert in Utah connects to my web server in California, which has the IP address of GRCcom, and verifies the contents of a specific file which they created for the purpose. The implicit and crucial assumption is that the packets DigiCert caused to be dropped onto the internet in Utah were actually routed to and received by the web server at GRCcom in California. Everything about the legitimacy of the certificate GRC has requested depends and relies upon the truth that DigiCert obtained that file from my web server and not from someone.
A so-called BGP prefix attack involves someone arranging to insert the network prefix for a small network into a big iron Internet router, which would then cause it to misroute any packets bound for any IP address within that small network prefix. In other words, the traffic for a specific network would be effectively hijacked. Following further with our example, if this were done to a router near DigiCert through which the packets bound for GRC was traversing, those packets would be sent not to GRC but presumably to an attacker. In doing this, the attacker's server not mine would be hosting the domain control validation file and they would be proving that they not I control the GRCcom domain, and DigiCert would then, having done their due diligence, issue them a web server TLS identity certificate for my domain, grccom. And here's the crucial point. Here's the crucial point the only way and reason this BGP router prefix hijack attack works, which, as Google's note mentionedCert's packet traffic destined for GRCcom would be flowing, could be compromised. While this compromise was in place and my web server at GRCcom was effectively unreachable by DigiCert, it would still be reachable by everyone and anyone else located anywhere else through other non-compromised routers. And this brings us to the need for MPIC multi-perspective issuance corroboration. And now we know what that term means, with the researchers at Princeton University's Center for Information Technology Policy having demonstrated the real-world feasibility of these BGP prefix hijack attacks.
Authorities going forward must perform domain control validation from multiple geographically diverse locations. Immediately, as of March 15th, bring that number up to three, and from at least two distinct regional internet registry regions. By June 15th of next year, 2026, that number grows to four, also from at least two RIR regions. And by the end of next year, December 2026, at least five remote network perspectives must be used in order to verify domain ownership and validation. Five, wow. So it's clear that once again these guys are not taking any chances. It would be so supremely difficult to somehow arrange to simultaneously intercept traffic originating from as many as five different locations that it's safe to say that this makes this mode of validation attack, you know, infeasible and takes it off the table.
2:59:59 - Leo Laporte
So that is.
3:00:00 - Steve Gibson
MPIC multi-perspective issuance corroboration, you know, verifying ownership of a domain from multiple perspectives on the internet, multiple locations.
3:00:13 - Leo Laporte
You can still screw up the border router, though, right.
3:00:17 - Steve Gibson
Yes, border gateway protocol.
3:00:21 - Leo Laporte
I mean, it's meant to be resilient, but it can happen. Yeah, this is cool.
3:00:26 - Steve Gibson
And I also wanted to note I heard your mention of the passing of the guy who Buffer bloat man, yeah, man, yeah and we and we talked about buffer bloat on the podcast and explained that it was. It was messing things up because the internet is designed to drop packets, and router man, consumer, router manufacturers thought, oh, we got so much ram, we'll have big buffers and then it'll be great that packets aren't dropped. Well, it messed everything up. What you's, not what you want, you want to drop him.
3:00:58 - Leo Laporte
Yes, he was only 59. He was a young guy. Let me see if I can pull up the story, because we did. We talked about it on this Week in Tech on Sunday and it was. It was a sad story.
3:01:10 - Steve Gibson
Do we know?
3:01:12 - Leo Laporte
We don't know what happened. No, the only reason I knew what happened is, uh, eric raymond. Uh, esr posted something on x? Um, eulogizing, uh. That's why I want to get the story, because I've forgotten his name now. But that's kind of the story in a way. Is this, this technology that uh saved all of us? Um, you know was, you know buffer, what was discovered and corrected pretty much yep, um, by this uh, one guy. So it's kind of a neat story. Let me see if I can. Uh, oh, shoot, where is his name? Um, we did so many stories. I'm looking through the show notes, uh, and I don't see it so, um, but yeah, it was a, it was a very uh the end.
Yeah, the podcast. Yeah, you'd think that these show notes would be in order, but his last name was taught, I think, t-a-h-t e I think it had an e on the end maybe it had an e on the end. Oh, now this is gonna make me mad, because I, I do want, I do think we should bring it up real quickly how about we just uh, what if we google buffer bloat?
google buffer bloat. Why is it not in the in the show rundown? That's the strangest thing. I must have accidentally deleted it after the show was over, or something okay, wikipedia's got a entry and I'll bet they give him credit, sure uh, dave tot t-a-h-t is his name and here's the eulogy from ericus raymond, who, of course, is a well-known open source guy.
Wrote the cathedral in the bazaar. He says dave taught. There's an umlaut over the a-t-a-h-t died. Yesterday, one of the unsung heroes of the internet. He uh discovered buffer bloat and then uh went out and and basically got router manufacturers to fix it. So it's, it's less of an issue uh right now. So, um, uh, something, something to note.
3:03:19 - Steve Gibson
Yeah, it says it gained more widespread. Wikipedia says it was initially described back in 85, and that, of course, predates this podcast, but it gained more widespread attention starting in 2009, and that's when you and I were together and we said, hey, let's talk about this. It's cool.
3:03:38 - Leo Laporte
There's his ex account. He lived in half moon bay um.
There's not much more, uh, except uh, that eric raymond lost him too young yeah and uh, and I guess, uh, he might have been on floss weekly back in March because Dave reshared a floss weekly link. So, yeah, unexpected, I think. I gather Dave taught a guy whose name very few of us know, even even those of us who know what buffer bloat is. But we do owe him a debt of gratitude. So thank you, dave, for what you did and thank you, most importantly, mr Steve Gibson, for what you do each week on this show. We do Security Now on a Tuesday, right after MacBreak Weekly. That comes out usually around 1.30 Pacific, 4.30 Eastern, 20.30 UTC, and I mention that because you can watch us live if you want. If you want the freshest security now we stream it for our Club Twit members. They have access to everything we do in the Club Twit Discord. In fact, we're doing more and more in there because it's such a great place to hang out. So if you're not a member, join Club Twit for $7 a month and you get ad-free versions of all the shows and you get access to the club twit discord and a lot of special events uh going on in the uh in the club at all times, including all the animated gifts anyone could ever want. A lot of fun. Um, anyway, if you are a club to a member, you can watch the show there it is. It's a gif. You can watch show uh in the club to a discord, but but you can also watch it anywhere you want. I mean, I'm just gonna leave this up for a while because they go crazy when they know they're on camera in the club. Uh, you can watch on YouTube. There's actually eight different streams the Discord, but there's also YouTube, twitch, TikTok, xcom, facebook, linkedin and Kik. So that's why you would need the time you can watch that live, but you can also get it after the fact Just by, just by. All right, I close it because it's it's distracting me just by uh going to the website twittv.
Slash sn steve has uh the show on his site. Actually, he has unique versions of the show that no one else has. He has a 16 kilobit audio version. It's a little scratchy but it's small. He has a 64 kilobkilobit audio version, which sounds great. We actually don't distribute that anymore. We do 128-kilobit audio for some technical reasons. He also has show notes, which are really great, and he has the transcripts written by Elaine Farris, so you can read along as you listen or search through the transcripts and find stuff. We've talked about All of that at GRCcom.
While you're there, it would behoove you if you have mass storage of any kind and I suspect you do, unless you're watching this show on a camera running linux. Even then it wouldn't be a bad thing to get a copy of spinrite, the world's best mass storage, maintenance, recovery and performance enhancing utility. 6.1 is the current version. It just came out and you can get it at GRCcom. You can also go to GRCcom slash email to get your email approved so that you can email comments and thoughts to Steve. That's the best way to do that. He also, as you can see, monitors X and other places, but email him.
And when you're there you'll see there's two checkboxes unchecked for the newsletters. One is, of course, the weekly mailing of the Security Now show notes. You'll get them a day ahead of time. You can read ahead, you can look at the picture of the week. You can prepare yourself for the Tuesday extravaganza, you can also. There's a second box, which is a very infrequent mailing when something big happens in Steve's life. The next one's probably going to be when he ships his DNS benchmark app the pro version of that sometime soon. He's working on it right now. Yep, it's working, it's coming along, it's exciting.
3:07:49 - Steve Gibson
You'll get the.
3:07:50 - Leo Laporte
you know the first information about it. So go to GRCcom. That's really my advice. It's a great way to hang. You can also subscribe in your favorite podcast player. We have audio and video available. That way you get it automatically. Your choice. It's a podcast and we appreciate the fact that you come by every week and listen. I tell you what I don't want to miss a Tuesday. I hope you won't either. Thank you, steve. We'll see you next time on Security Now. Thanks, my friend See you then Bye.
Apr 8 2025 - Multi-Perspective Issuance Corrobo…
IoT Done Right, France Phishes, Gm… All Transcripts posts Contact Advertise CC License Privacy Policy Ad Choices TOS Store Twitter Facebook Instgram YouTube Yes, like every site on the Internet, this site uses cookies. So now you know. Learn more Hide Home Schedule Subscribe Club TWiT About Club TWiT FAQ Access Account Members-Only Podcasts Update Payment Method Connect to Discord TWiT Blog Recent Posts Advertise Sponsors Store People About What is TWiT.tv Tickets Developer Program and API Tip jar Partners Contact Us